Steps to Schedule Your Vulnerability Assessment:
1. Schedule a 30-minute Discovery Session
2. We determine IF and HOW we can help
3. We provide a Tailored Proposal
4. Together, we review the Proposal
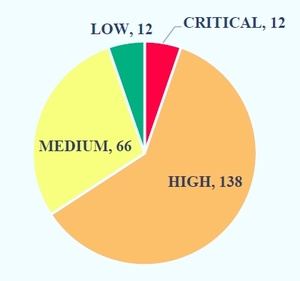
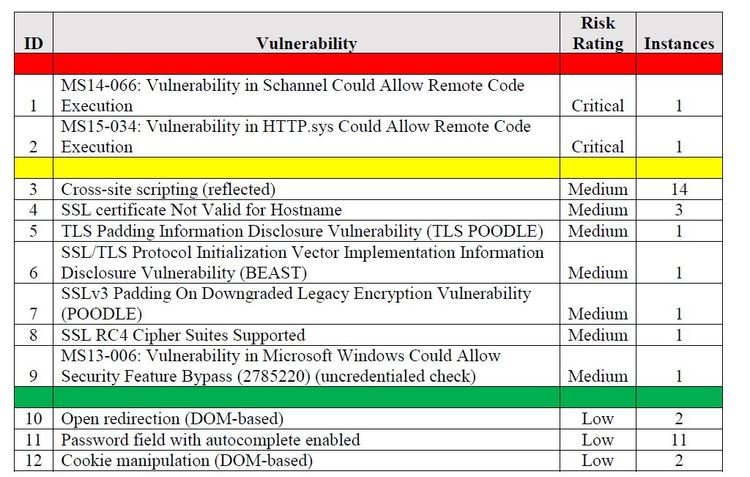
A Vulnerability Assessment is the process of evaluating assets in an enterprise for missing patches and misconfigurations. Often the vulnerability assessment is in support of regulatory compliance or compliance with a standard. The process identifies and prioritizes vulnerabilities based on criteria such as the likelihood of the vulnerability being exploited and the severity of the vulnerability – what the vulnerability provides the attacker when used. These criteria are used to categorize the vulnerability as Critical, High, Medium, Low, or Informational.
We assess systems using vulnerability scanning tools and manual methods to identify and prioritize findings based on the criticality of system vulnerabilities. We scrub findings to eliminate false positives and prioritize risk, based on existing security controls for your environment. The Vulnerability Assessment looks for missing patches and existing vulnerabilities for each system. We use authenticated scans wherever possible to reduce false positives and improve accuracy.
We typically perform a Vulnerability Assessment on an internal enterprise environment and a Penetration Test against the external, public-facing systems. We can, however, perform a Vulnerability Assessment against your external systems and wireless systems as well.