Overview
Have questions or interested in a penetration test or assessment? Complete the form below and we'll get back with you right away. We appreciate your interest.
Web Application Penetration Testing
Steps to Schedule Your Penetration Test:
1. Schedule a 30-minute Discovery Session
2. We determine IF and HOW we can help
3. We provide a Tailored Proposal
4. Together, we review the Proposal
Are your web applications secure? We can validate this for you with a Web Application Penetration Test (Black and Gray Box). Web applications are the most frequently attacked items on the Internet and are often the most insecure.
Highlights
- Highly trained and certified penetration testing team: CISSP, CSSLP, OSCP, ECSA, LPT(Master), CEH, & more
- Proven penetration testing methodology
- Includes remediation validation test (RVT) to validate your fix actions
- Clear & concise reports with prioritized, actionable items
Deliverables
- External Web Application Penetration Test Report
- Report findings review with your team via an online session
- Remediation Validation Test (RVT) after you fix identified problems
- Letter of Attestation
Guarantees
If we do not find at least one vulnerability with a risk rating of Low or greater, we will refund 100% of your money, minus any incurred expenses.
Avoid the 7 Deadly Mistakes Choosing Penetration Testing
We emulate an attacker by utilizing similar techniques to perform reconnaissance, identify vulnerabilities, and break into your systems. Unlike an attacker, however, we stop our test before exposing sensitive data or doing harm to your environment. With the Black Box (Unauthenticated) Penetration Test, this means we have unauthenticated access and have little prior knowledge, except the URLs, about the systems in scope. We will also perform a Gray Box (Authenticated) Penetration Test of each system, as applicable, after the Black Box Penetration Test. With a Gray Box Penetration Test, we have “user” level knowledge about and access to a system. A Gray Box Penetration Test is used to test an application that supports multiple users by testing authenticated user access to ensure a user on an application cannot access another user’s data or escalate privileges. We test an application, such as a web application or custom-built application as an authenticated user. We log on to the application as that user and perform testing to see if we can perform any of the following:
Horizontal Privilege Escalation – where an authenticated user can access another user’s data. An example of horizontal privilege escalation is a bank application, where an authenticated user’s account number shows up in a URL. If I can change the account number in the URL to another account number and access another user’s banking information, I’ve just performed a horizontal privilege escalation.
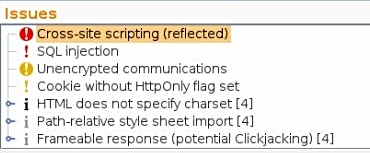
Vertical Privilege Escalation – where an authenticated user can escalate privileges to an administrator-level account. An example of this is a web application that has a value representing the username in a hidden field that is returned after successful authentication. What would happen if we changed the value from ‘username’ to ‘root’ or ‘administrator’ and passed this back to the web application server?
We ensure our testing covers the latest Open Web Application Security Project (OWASP) Top 10, along with the following:
Many Web Applications are vulnerable to injection attacks, such as SQL Injection
- SQL injection (Blind, Inference, Classic, Compounded)
- OS command injection (Informed, Blind)
- Server-side code injection
- Server-side template injection
- Reflected XSS
- Stored XSS
- Reflected DOM issues
- Stored DOM issues
- File path traversal / manipulation
- External / out-of-band interaction
- HTTP header injection
- XML / SOAP injection
- LDAP injection
- CSRF
- Open redirection
- Header manipulation
- Server-level issues
We think it is better to have an ethical hacker find the holes into your enterprise than an adversary. Our Web Application Penetration Testing Services provides details on exploitable web vulnerabilities in a prioritized, tangible manner. Our report allows you to better understand what your web server or web application look like from an attacker perspective; what the “attack surface” looks like. This helps you prioritize efforts to mitigate risk to reduce breach likelihood.
Not only do our Web Application Penetration Testing Services show you what your attack surface looks like to an adversary, but they can be used as a safe way to test your organization’s incident response capabilities. Our Penetration Testing services can also be used to tune and test your security controls, such as your IDS, Firewall, Web Application Firewall (WAF), Router Access Control Lists (ACLs), etc.
Our Web Application Penetration Testing services also help you meet compliance audit requirements such as HIPAA, PCI DSS, and NIST.
You get four items:
- Penetration Test Report
- Penetration Test Report Findings Review with your team via an online session
- Discounted Retest Option for a rerun of the Web Application Penetration Test after you fix identified problems
- Letter of Attestation
1. Penetration Test Report
The Penetration Test Report includes the URLs and IP addresses tested, reconnaissance (discovery) information, vulnerabilities discovered, steps taken during the assessment, exploitable areas, and prioritized recommendations. For any systems we are able to exploit, an Issue Detail section is used to discuss step-by-step the process we used to gain access, escalate privileges, etc.
2. Penetration Test Report Findings Review
We schedule either an in-person of online session with you where we walk through the report with your team and answer any questions about the findings, our methods, or the steps required for remediation. Many competitors deliver a confusing lengthy report at the end of the engagement for you to decipher. Our penetration test report review adds tremendous value because we can clarify findings and remediation steps.
3. Discounted Retest Option
How do you know the steps you took to fix our penetration test report findings actually worked? Validation removes the guesswork. When you’re ready, after fixing the issues identified in the penetration test report, we offer a deep discount to rerun the same penetration test. This is a crucial and often overlooked step in this process. Validating security controls, patches, and other fix actions is extremely important. We have discovered numerous organizations that thought they fixed a finding we identified, only to discover after a retest that the finding was still there.
4. Letter of Attestation
The attestation letter serves as record of us performing the penetration test. It includes a summary of the findings. Its intent is for external use, outside of your organization, to show proof that a security assessment was performed and to highlight test results.
Frequently Asked Questions
