Here are seven steps to exploit a vulnerable system with almost no experience.
Disclaimer: You need written permission/authorization to perform a penetration test (hack) on a system owned by someone else. Yes, even if it is someone you know or a friend. Remain ethical – run your tests against your own targets or obtain permission (written).
Setup
- Download the Prebuilt Kali Linux VMware or VirtualBox Image.
- Download VMware Workstation Player or VirtualBox.
- Unzip Kali and open with VMware or VirtualBox.
Exploit
1. Log on to Kali (root/toor).
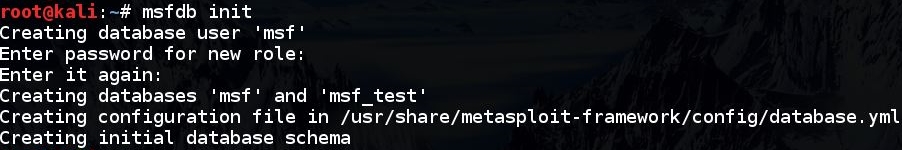
2. Create the Metasploit database by opening a terminal window and running “msfdb init”:
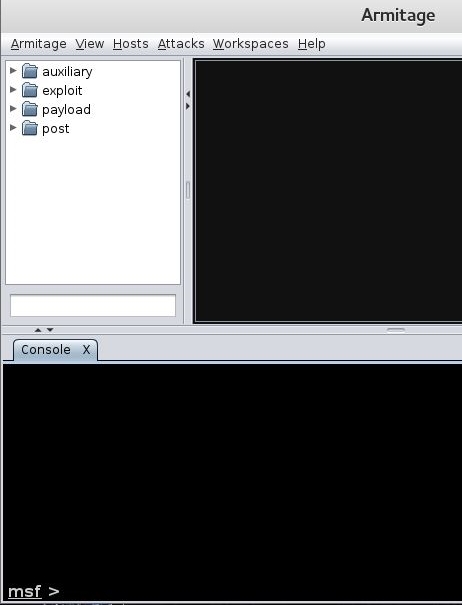
3. Run Armitage by typing “armitage” in the terminal window and hitting enter.
Accept the defaults for the rest of the Armitage screens:
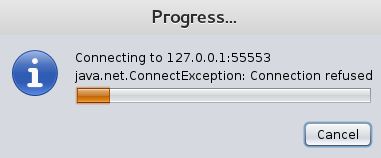
While the Metasploit RPC server starts in the background, you will see a connection refused message. This is normal and should go away once the backend Metsaploit RPC server starts for Armitage (Metasploit GUI frontend).
Armitage should finally start and you should see a GUI:
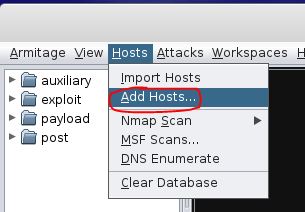
4. Choose the target (host or range of IP addresses) to attack:
Select “Add Hosts…”:
Enter the target (hosts) IP addresses, then click Add. In this example we entered 10.1.1.22.
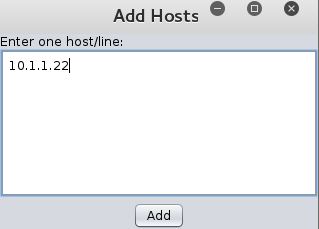
Armitage Add Hosts Window
It may take a second for the target to appear in the Armitage target window.
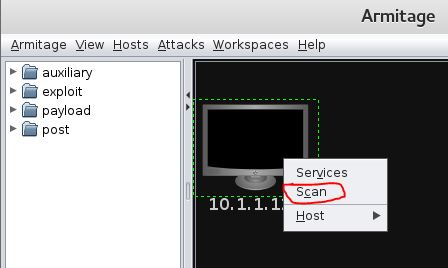
5. Scan the target(s) for open ports, services, operating system, etc.
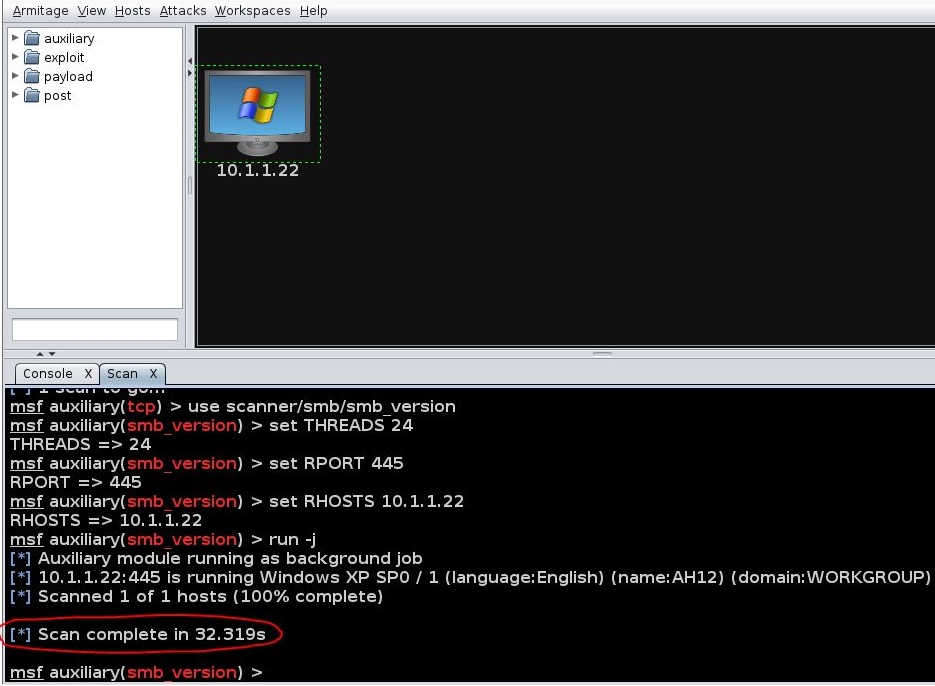
Right-click on the target and choose scan:
When the scan is complete you should see a message at the very end in the Armitage “Scan” window that states “Scan complete in 12.345s”. This means the scan is completely finished:
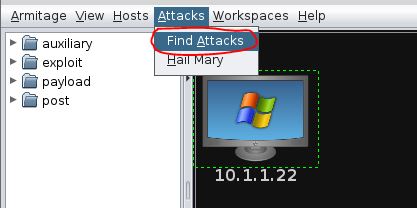
6. Find Exploits
Click on “Attacks” in the Armitage menu, then select “Find Attacks”:
It may take 30-45 seconds for the Progress to complete. When finished you should get the “Attack Analysis Complete…” message:
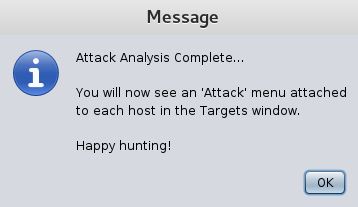
Armitage Attack Analysis Complete…
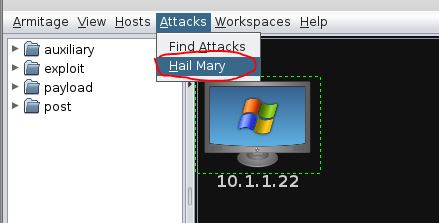
7. Launch Exploit(s)
In this case, we’ll do a “Hail Mary” attack. The Hail Mary is not very stealthy because it will try every attack that Armitage thinks may work against the target. This is not very surgical, but often effective.
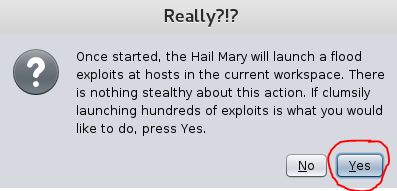
Click on “Yes” to the Armitage Really?!? warning.
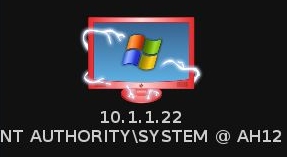
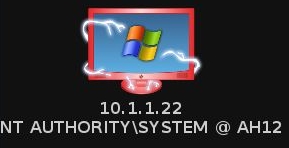
If one of the many attacks the Hail Mary tried works, you may get a Meterpreter session, represented graphically by the lightning looking hands around the red target:
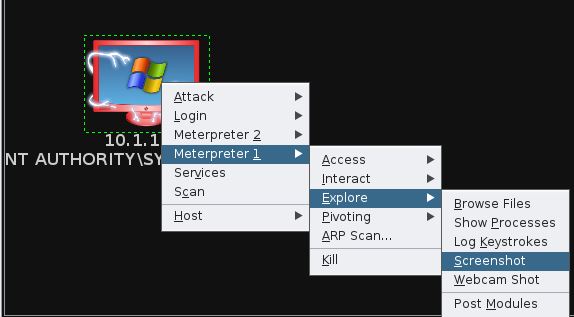
From here you can do whatever you want… Play around with the Meterpreter shell to dump hashes, take screenshots, log keystrokes, etc., from the victim:
That’s it. Congratulations on your hack!