Windows Task Manager serves a purpose, but we recommend you replace it with Process Explorer for many reasons. A few of the reasons for using Process Explorer:
-
It is Free.
-
It easily integrates with VirtusTotal.
-
It shows process dependencies / process trees.
Here is the information Windows Task Manager shows you:
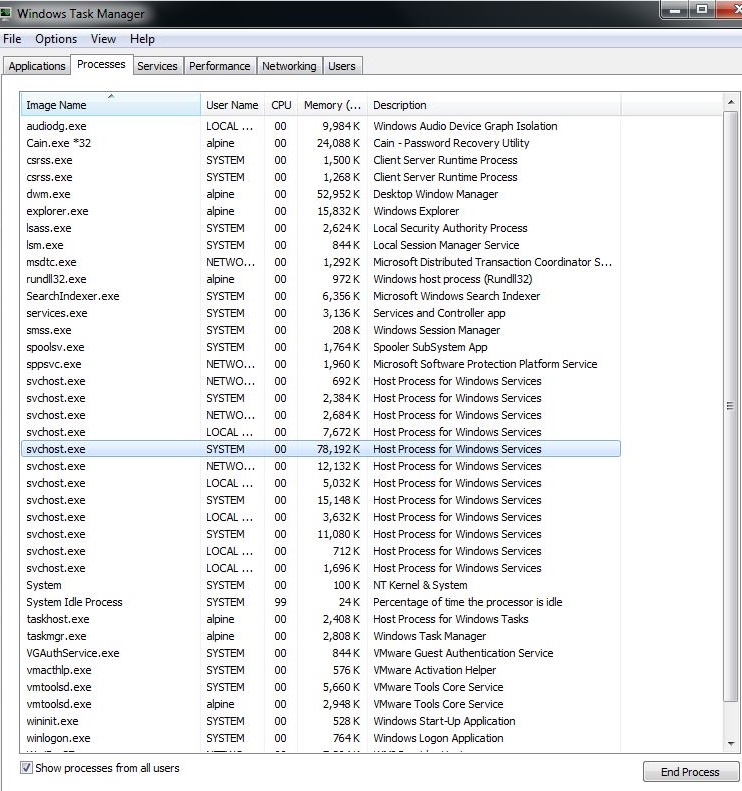 Windows Task Manager
Windows Task Manager
Here’s the same information shown with Process Explorer:
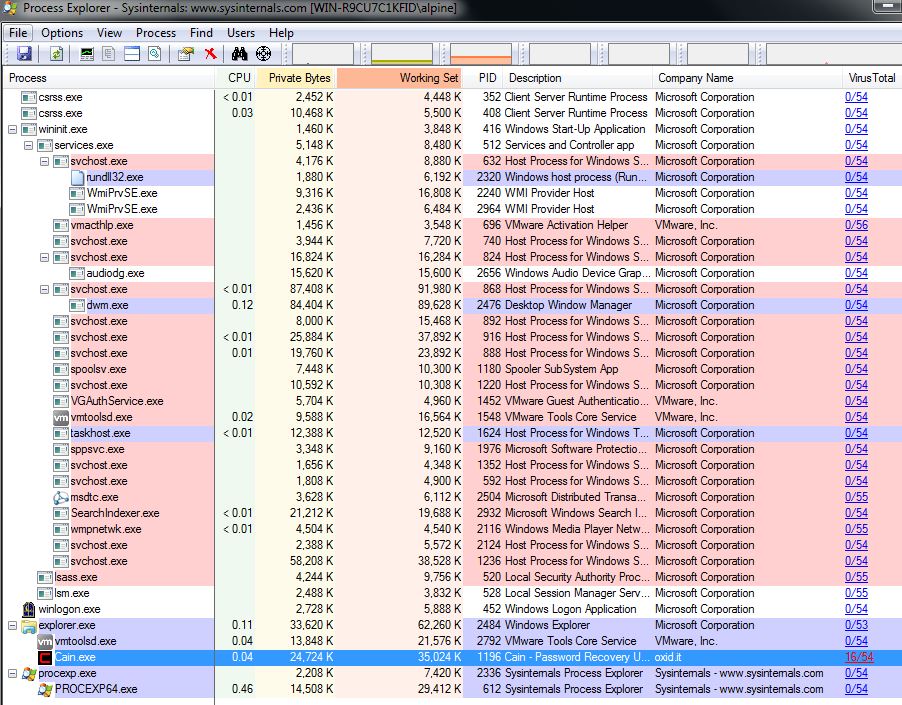 Process Explorer
Process Explorer
As you can see in Process Explorer – the process “Cain.exe” was flagged as malicious by 16 out of 54 Anti-malware vendors on VirusTotal.
How do you replace Windows Task Manager with Process Explorer? Here are the steps:
1. Download Process Explorer or the entire Sysinternals Suite from here, the legit Microsoft site:
We recommend the Sysinternals Suite, as it has many other useful tools.
2. After you extract either download in Step 1, run Process Explorer (procexe.exe) by double-clicking on it.
3. After Process Explorer starts and you accept the EULA, go to File and choose Show Details for All Processes

4. Go to Options and choose Replace Task Manager
5. Go to Options and choose VirusTotal.com and select Check VirusTotal.com



