At the inception of the computer age, computer hacking was limited to elite hackers – those with high-level computer science knowledge. Many of them, known as white hat hackers or blue hat hackers, aimed to strengthen computer systems security through finding weaknesses. PCMag.com describes white hat hackers as “people who break into a computer system and inform the company that they have done so. They are either concerned employees or security professionals who are paid to find vulnerabilities. White hat hackers are the ‘good guys.'”
But the days of a hacking culture dominated by good guys are long gone. A report produced by usaid.gov states that “cyber crime has been increasing in complexity and financial costs since corporations started to utilize computers in the course of doing business. As technology increases between governments that are involved in international business, criminals have realized that this is a cost-effective method to make money.”
Over the decades, cybercrime has evolved, branching out into many strains. There are black hat hackers – (the criminally motivated). crackers, (those breaking into systems to steal information), hacktivists, (infiltrators of computer systems to use them as platforms for public movements), and script kiddies, defined by WiseGeek.com as “teenagers who use readily available tools written by experienced hackers to deface websites or break into computer systems, usually done for peer recognition and attention.”
As computer technology has grown integral to personal and business endeavors, and as dependency on computers has increased, the impacts of cyberattacks have escalated. NetStandard.com reported that in 2014, the US was hit with 5,000 cybersecurity attacks every hour, and the Pentagon sees 10 million hacking attempts per day. Mark VanOrden, the CIO of the Utah Department of Technology Services reports on KSL.com that “two years ago, the average number of cyber attacks was approximately one million malicious attacks per day. Now, the attacks are up to 20 million per day,” and this just within Utah’s secure government networks.
Cyberattacks pose a greater danger now than in the past because, as technology improves, the technology used to conduct cybercrimes becomes more accessible, easier to use, more effective, and more dangerous. According to cybersecurity expert Lloyd Borrett, “not all cybercriminals have sophisticated computer and networking skills. Today, the vast majority of cybercriminals simply use the malicious tools and kits marketed for profit by those creating them.” He goes on to say, “in effect, most cybercriminals are simply up-to-date script kiddies, but now they’re motivated by profit, not notoriety. For about US$400, almost anyone can buy appropriate scripts and after about four hours of working through the instructions, be fully set up as a cyber-criminal. Scary stuff.”
Script kiddies, motivated by peer competition and oftentimes oblivious to the implications of their hacking, are capable of wreaking havoc using readily available resources such as password cracking tools, packet sniffers, denial of service (DOS) tools, port scanners, and integrated attack tools. Computerworld.com quotes Mandy Andress, president of ArcSec Technologies, Inc., as stating, “The fact that script kiddies will blindly launch scripts against large IP blocks without any thought as to who they are attacking makes them dangerous, especially for those administrators who do not take security seriously.”
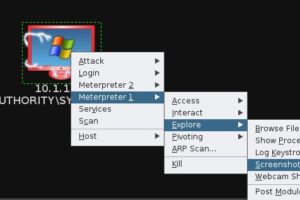
Script kiddies, having little computer science training or skill, can gain basic knowledge of hacking resources such as Kali Linux, Armitage, and Metasploit, and they can even contribute to the attacks of more capable, more dangerous elite hackers, sometimes without even knowing it. According to Computerworld.com, “script kiddies—mostly teen Web page defacers—often unwittingly aid and abet serious criminals through their reckless probing and compromising of systems… the more sophisticated criminals are then able to exploit the work of the script kiddies while remaining anonymous.”
Using phishing schemes such as link manipulation, website forgery, and pop-ups, script kiddies are capable of inflicting major damage. In June 2017, ZDNet.com reports that script kiddies were likely responsible for a major diplomatic crisis when a television station in Qatar was compromised and false information planted. According to the website, “the hackers were reportedly able to take complete control of the news agency’s web server, content management system (CMS), and all social media accounts. The hack itself was ‘nothing special,’ but still was able to compromise the ‘entire QNA.'”
The impacts of cybercrime committed by script kiddies and more proficient hackers are not only economical – there are psychological and social impacts as well. Endnotes.com points out that social and psychological professionals are called upon to “help victims cope with the fallout from identity theft, sexual abuse, or financial ruin.”
As computing technology continues to evolve, so will hacking and the infiltration tools accessible to cybercriminals, whether low-skilled script kiddies or elite hackers. Steve Taylor, contributor to Forbes.com, reports that “from 2013 to 2015 the cybercrime costs quadrupled, and it looks like there will be another quadrupling from 2015 to 2019. Juniper research recently predicted that the rapid digitization of consumers’ lives and enterprise records will increase the cost of data breaches to 2.1 trillion globally by 2019.”
To protect yourself, Anthillonline.com recommends having Internet security in place on all computer devices, limiting users, and utilizing strong passwords. They also suggest that “giving up administrator privileges is a simple way to remove 90% of the risk of malware.”
Organizations aiming to secure themselves against cyberattacks can take proactive measures, such as running run phishing exercises, risk assessments, audits, penetration tests, implementing digital forensics services, and training personnel. Alpine Security can assist with cybersecurity assessment and testing services as well as cybersecurity training, offering trainers who have practical, real-world experience. Their trainers work as penetration testers, incident response handlers, forensic analysts, auditors, etc. We offer both Live In-Person and Live Online certification training. Our courses include the exam voucher and have an exam pass guarantee. We guarantee findings with our penetration testing and phishing campaigns. We are based in the Greater St. Louis area and add value to clients worldwide.