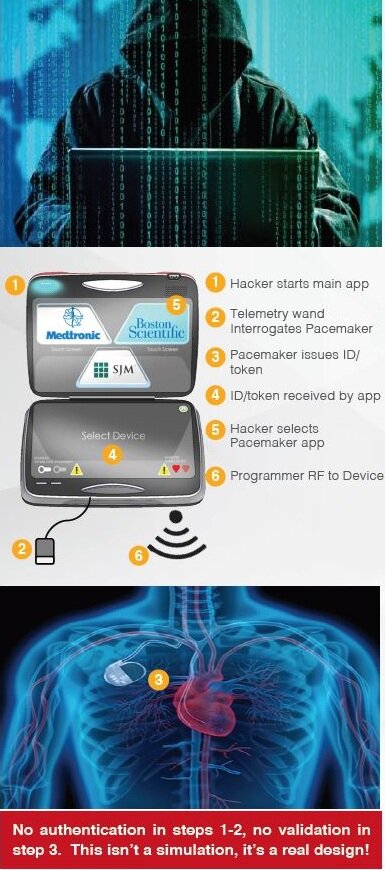
Steps to Hack a Pacemaker
When people talk about medical device security, the conversation often turns to data security and HIPAA. There’s plenty to be said about protecting patient privacy, but patient safety is a greater concern.
Patients are connected to the internet more than they have ever been before, thanks to the increasing scope of what is now being called the Internet of Medical Things. In 2018, Allied Market Research predicted that the IoMT would reach $136.8 billion by 2021.
Connected devices allow doctors to receive real-time diagnostic and treatment information and adjust therapies from anywhere. They’re a great solution for a system that’s trying to care for a growing population with limited resources, but they are also highly vulnerable to attack.
The Problem with the Solution
Whenever an industry moves through a period of significant growth, it has to guard against progressing too fast. In the case of healthcare cybersecurity, this can be a matter of life or death.
Patients with pacemakers and insulin pumps depend on these connected devices. If there are vulnerabilities in the software that tell these devices what to do, a hacker could change those instructions and seriously harm the patient.
At the 2018 Healthcare Security Forum, Drs. Tully and Dameff showed a video of a simulated breach to show the possible effects of medical device hacking. The scenario involved a simulated patient whose hacked pacemaker was shocking him unnecessarily, repeatedly sending him into cardiac arrest before reviving him again.
The medical team had never seen a case of this type, nor had a cardiologist on the phone, and ultimately emergency surgery was performed to cut the lines that power the pacemaker. The simulation proved to be illuminating for the team and those who viewed the videos, all of whom had the chance to see the suffering and possible death of a patient who had become the victim of hackers.
Drs. Tully and Dameff expressed concern that despite the knowledge that this could happen, decision-makers may not see it as a priority until it happens in real life. Yet in the first quarter of 2018, according to Healthcare IT News, medical device recalls reached record high levels. The most common reason?
Software vulnerabilities.
Known Security Issues
More than a year later, security vulnerabilities still plague certain critical medical devices.
In June of 2019, the FDA issued a warning that Medtronic MiniMed’s insulin pumps had a vulnerability that could allow a well-equipped attacker to change the pump’s settings using unauthorized radio signals. An affected patient could experience dangerously low or high blood sugar, potentially at life-threatening levels.
The FDA recalled the pumps and provided patients with more secure alternatives.
Experts have also identified 11 specific cybersecurity vulnerabilities in operating systems that run IPnet, a software used in numerous medical devices. Because IPnet lets connected computers communicate with one another, a hacker could attack multiple patients with one piece of malware.
There have not yet been any specific reports of patient harm resulting from a hacked device or connected network. However, FDA’s Center for Devices and Radiological Health emphasizes that the risk is too great to wait for an incident.
Furthermore, says FDA deputy director Suzanne Schwartz, attacks can occur without the user’s participation and even without their knowledge. If we continue to wait for a high-profile incident, we could miss many smaller but no less insidious events.
The Role of Antiquated Systems
Patient devices are connected to hospital or care system networks, which are often highly antiquated from a cybersecurity standpoint. In many cases, they lack the resources to update those systems.
In their aforementioned presentation, Drs. Tully and Dameff shared a case study involving a patient who was experiencing a stroke. They explained that the patient depends on a vulnerable pacemaker as well as a care system that uses a highly hackable network. If such a network does get hacked, medical professionals can’t communicate the information they need to give life-saving care.
The point isn’t merely hypothetical. A 2018 study published in the Journal of the American Medical Association revealed that out of 1,503 analyzed breaches, 70 percent targeted care delivery organizations.
Addressing Trust in Technology

Most doctors trust medical devices and rarely consider potential cybersecurity implications
The lack of known fatalities from hacked devices is feeding one of the most dangerous patterns in medical technology – the unquestioning trust of doctors in the technologies that keep their patients safe.
Doctors are trained to trust in medical technology. In many situations, they need to maintain that trust so they can focus on the patient. But when it comes to protecting that patient against attack, a degree of skepticism is healthy.
Several years ago, physician-researchers Jeff Tully and Christian Dameff presented a group of fellow physicians with hacked devices. When they asked their subjects to identify any devices that were compromised, the doctors incorrectly reported that all devices were secure.
When medical professionals have this kind of unquestioning trust in connected devices, the patients carry most of the risk.
Existing Regulations: Privacy vs Safety
In 2018, security researchers Billy Rios and Jonathan Butts created a simulation that showed what could happen if hackers got into a pacemaker or insulin pump. They demonstrated that the hacker could reprogram either device from any location, potentially hurting or killing the patient.
Following this demonstration, the FDA began to issue more regulations and recommendations specific to patient safety.
The FDA’S 2014 premarket submissions guidelines focused jointly on data threats and safety to a relatively similar degree. A revised draft of the same document issued in 2018 adds specific language addressing security concerns that could “result in patient illness, injury, or death.”
The draft also divides threats into tiers, the higher-risk tier involving those devices for which a security incident could “directly result in patient harm to multiple patients.”
What’s more, the safety communications issued by the FDA since 2018 have almost exclusively focused on patient safety. Privacy-related regulations such as HIPAA are still in effect, but what good is privacy if the patient doesn’t make it?
The Takeaway for Tech Professionals
The world of medical device safety is still in its infancy. After years of focusing on data security and patient privacy, clinicians and regulators are starting to see the more serious implications of an attack on a patient.
The field is primed for innovation.



