Hacked medical devices could be the next big security nightmare. There are currently between 10 and 15 connected devices per hospital bed in the United States, many of which are vulnerable to attack. The increased use of pacemakers and other embedded devices also leaves patients at risk, with many of these devices using radio or network technology. While connectivity does increase the amount of data available to physicians and can lead to better outcomes for patients, it can also be incredibly dangerous unless stringent security measures are taken.
Anything that connects wirelessly to other equipment can be compromised, with historically low levels of security on medical instruments and embedded devices already linked to a number of security attacks. From debilitating ransomware attacks and the theft of sensitive medical records through to hacked cardiac defibrillators and pacemakers, a range of vulnerabilities in connected medical devices have already been uncovered.
Let’s take a look at five of the most dangerous hacked medical devices and analyze the steps being taken to ensure future security.
Pacemakers

Abbott / St Jude Medical’s Accent MRI pacemaker. Recalled due to cybersecurity vulnerabilities. Photograph: Abbott / St Jude Medical
Pacemakers were recently implicated in a major hacking risk, with 465,000 devices from Abbott’s recalled by the US Food and Drug Administration (FDA). According to authorities, hackers could endanger lives by remotely causing the batteries in pacemakers to go flat or forcing the life-saving devices to run at potentially deadly speeds. The identification of this risk has affected people in many countries, with Abbott’s (formerly St Jude Medical) being one of the biggest medical device manufacturers in the world.
The idea of hacking a pacemaker was first identified by the popular TV show Homeland back in 2012. In a case of fact following fiction, former US vice-president Dick Cheney and his cardiologist ordered the manufacturer of his pacemaker to disable its wireless capabilities. The connectivity or “remote monitoring” used by the latest generation of pacemaker devices makes them an ideal candidate for hacking, with this technology designed to allow cardiologists to monitor how well these devices are functioning.
In 2016, medical device research firm MedSec publicly revealed several vulnerabilities in St Jude Medical pacemakers related to the use of this technology. It’s important to note, however, that all pacemakers enabled with “remote viewing,” regardless of their manufacturer, can potentially be hacked. While there have been no reported cases of malicious intent so far, security enhancements for pacemakers and other implantable devices are being addressed by manufacturers and regulatory authorities through firmware updates.
In order to ensure security, patients needed to attend hospitals and clinics to update their firmware. While no invasive surgery was needed, the update could only be installed by trained medical staff. If you have a pacemaker, it’s important to realize that the low risk of being hacked is far outweighed by the benefits of remote monitoring. While it’s important to receive security updates as soon as they come out, people who are monitored remotely by cardiologists have been found to live longer, have better battery life for their device, have fewer inappropriate shocks and malfunctions, and have improved overall health management.
Drug infusion pumps
In September 2017, the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) identified problems with a number of syringe infusion pumps in U.S hospitals. A total of eight security vulnerabilities were found in the Medfusion 4000 Wireless Syringe Infusion Pump, which is manufactured by the medical device maker Smiths Medical. As part of the U.S Department of Homeland Security, ICS-CERT is responsible for reducing risks within and across all critical infrastructure sectors, and partnering with law enforcement agencies and the intelligence community.
Several vulnerabilities were recognized in the drug infusion pumps, which are typically used for the fluid delivery of nutrients, insulin, other hormones, antibiotics, chemotherapy drugs, and pain relievers. The devices in question are used across the world for the delivery of small doses of medication in the context of acute critical care, including neonatal intensive care, pediatric intensive care, and operating room procedures. The security threat detected could allow a remote attacker to gain unauthorized access and impact the intended operation of the pump, including the administration of fatal overdoses.
Specific high-severity security flaws identified:
- The use of hard-coded usernames and passwords to automatically establish a wireless connection if the default configuration has not been altered.
- A buffer overflow bug that could be exploited for the remote execution of nefarious code on the target medical device.
- Lack of authentication when the pump was configured to allow FTP connections.
- Presence of hard-coded credentials for the pump’s FTP server.
- Lack of proper host certificate validation, leaving the pump vulnerable to Man-in-the-middle (MiTM) attacks.
MRI systems
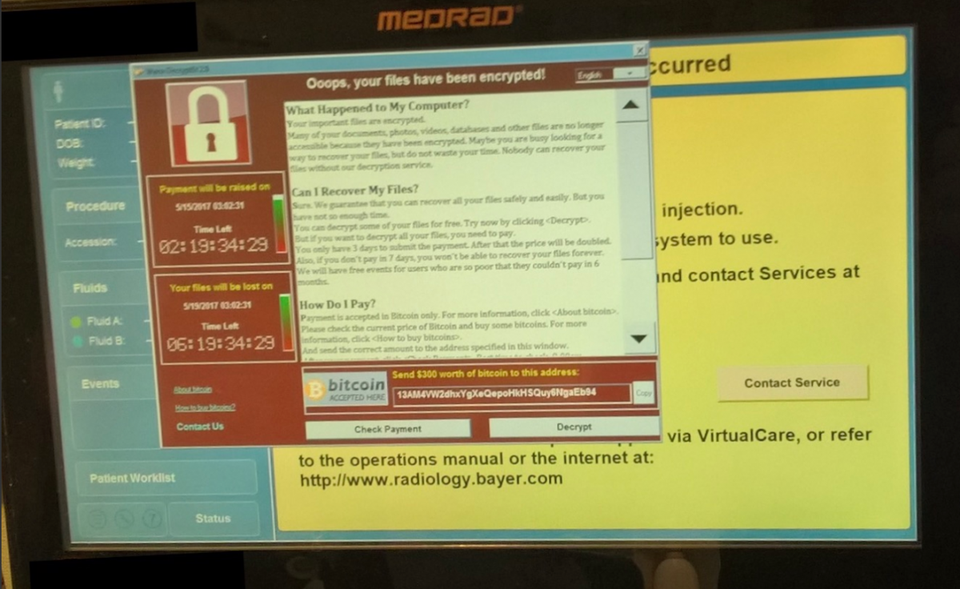
Back in May 2017, North Korea may have used a stolen National Security Agency (NSA) hacking tool to infect medical devices at U.S. hospitals. While the evidence is still unclear, what we do know is that as many as 200,000 Windows systems in hospitals and medical centers were broken into. Ransomware was a common payload delivered to these systems, but given the attack compromised the systems at the “administrator’ level, any type of payload could have been delivered. Overall, the attack affected 48 hospital trusts in the U.K. and an unknown number of medical facilities across the United States. At least one hacked Bayer Medrad medical device was discovered, a highly sensitive piece of radiology equipment designed to help improve medical imaging.
The infected Bayer Medrad device was the first time that a medical device had been hacked in the United States. The device in question is used for monitoring what’s known as a “power injector,” which helps to deliver a “contrast agent” to a hospital patient. These chemical agents are designed to improve the quality of magnetic resonance imaging (MRI) scans, which are used in detecting everything from trauma and stroke through to tumors of the brain and spine.
When they were made aware of the attack, Bayer sent out a Microsoft patch for the imaging equipment and all of their other Windows-based devices. The firm recommended that all hospitals made contact with Bayer’s Technical Assistance Center in order to receive continuing support and reduce device downtime. While this ransomware attack did not necessarily threaten patient safety directly, it did stop scanning machines from working for an extended period of time. This lack of function could trigger a number of clinical mistakes, including an increased need for hospital resources and unnecessary medical care delays.
Heart Rate Monitors

An ICD can deliver a shock to the heart. Modern ICDs can also function as pacemakers. The Medtronic Maximo was discovered vulnerable to cyberattacks.
The University of Washington discovered a serious security vulnerability in heart rate monitors in 2008, including the Medtronic Maximo. Also known as implantable cardioverter defibrillators (ICDs), heart rate monitors are used to treat abnormal heart conditions. These devices are surgically implanted in the chests of heart patients, where they can produce a concentrated electrical charge that shocks the heart out of ventrical fibrillation. This heart-attack condition occurs when the heart muscle twitches randomly instead of pumping blood in a coordinated fashion. According to the study, all that was needed to hack into this heart rate monitor was an oscilloscope, a computer, a wireless radio, and some free software.
This hack did not rely on a network and was made possible due to the inclusion of a small radio in each ICD device. While the inclusion of radio allows the device to be reprogrammed by a hospital doctor, it also makes these devices vulnerable to attack. Because the radio signal is not encrypted, anyone with basic equipment could make the device deliver a big enough shock to induce ventricular fibrillation, a potentially lethal arrhythmia, and the very thing these devices are designed to treat. While the potential of an attack is relatively low in comparison to pacemaker attacks that can abuse network connectivity, future versions of ICDs that are likely to send radio signals ten meters will require much more stringent security measures.
Hospital Networks
The biggest threat to medical security involves the shutting down of entire hospital networks. Instead of focusing on individual patients and their embedded devices, ransomware hackers are more likely to attack entire hospital systems. There have been numerous ransomware attacks on health care providers over recent years, including the WannaCry attack which devastated the U.K.’s National Health Service (NHS) and numerous U.S hospitals. These attacks, which used security flaws in Microsoft operating systems, highlighted just how unprepared hospitals were in dealing with this brave new world.
When hospital networks are attacked, it’s not just patient records that are compromised. As we have already seen with the hacked Bayer Medrad medical devices, much of the equipment used in hospitals are tightly connected. While radio replay and network vulnerabilities like those discovered in ICDs and pacemakers are the most common flaw found in individual devices, breaking into hospital networks could allow attackers to target multiple patients by sending incorrect information to physicians and targeting specific pieces of medical equipment.
In order to tackle this huge problem and stop more medical devices from being hacked, medical device assessment and penetration testing services are needed for hospital equipment and embedded devices. It’s also important that healthcare organizations are aware of the negative impacts of connectivity so that they can design security measures in their systems right from the outset. Robust long-term security is dependent on ongoing conversations between medical-device manufacturers, health care practitioners, the FDA, and security researchers.