Criminal hiding behind a mask turns up on computer screen asking the owner for money. Concept of phishing and ransomware, where the computer has all files on the harddrive encrypted and the victims need to pay a ransom in order to get their files unlocked.
The rising instances of ransomware attacks is harrowing to say the least. Attackers seek to achieve quick financial gains through the use of this tactic and to be frank, it is working.
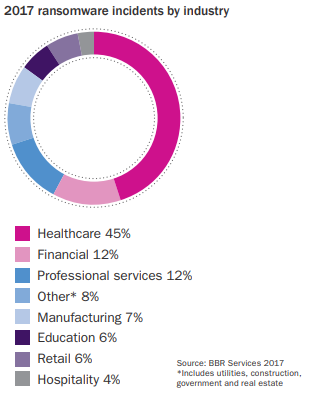
Ransomware is a type of malware that is spread through many different avenues. Organizations may run into a situation where an employee was sent a phishing email with a malicious link in it that redirects web traffic and downloads the ransomware to the user’s machine automatically. This is the most common tactic attackers will use to spread their ransomware, coming just ahead of using a spoofed website as seen in the image below:
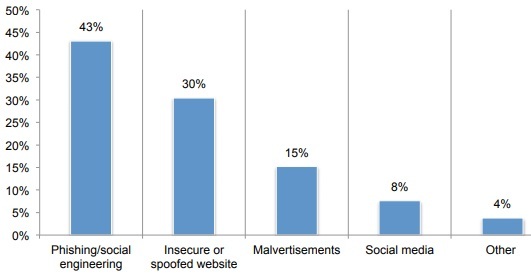 Source: Ponemon Institute, https://www.ponemon.org/local/upload/file/Ransomware%20Report%20Final%201.pdf
Source: Ponemon Institute, https://www.ponemon.org/local/upload/file/Ransomware%20Report%20Final%201.pdf
How Does the Ransomware Work?
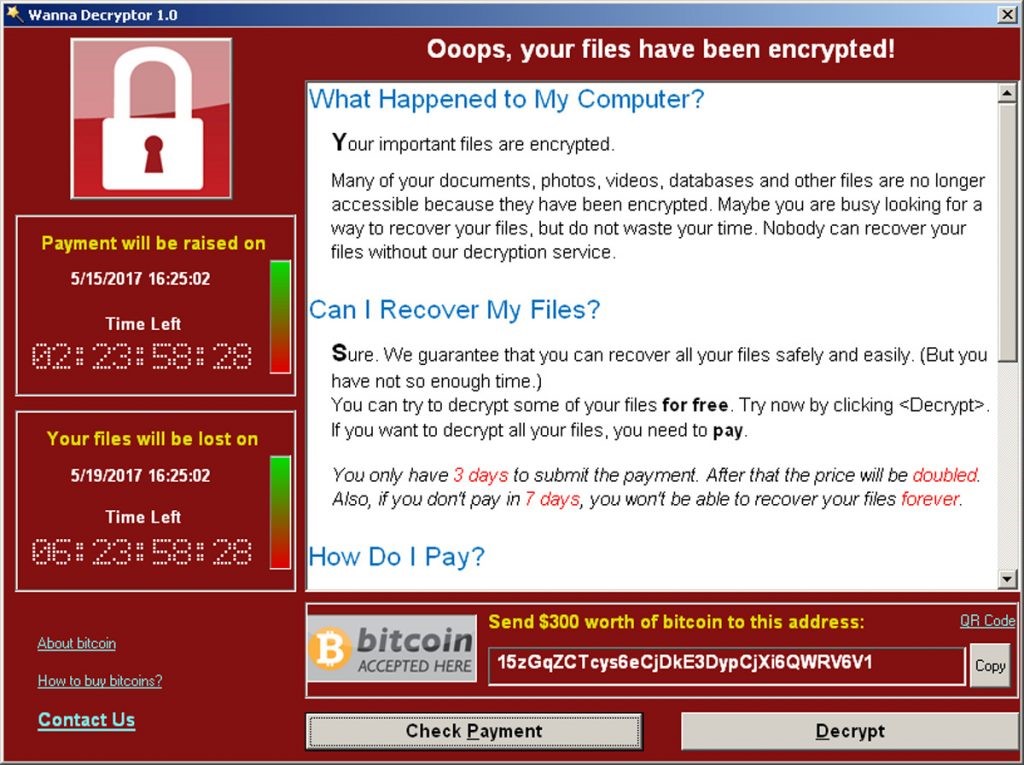
Once the ransomware is present on a machine, it starts the process of encrypting the hard drive, leaving the user with no access to any of the documents that they were working with, or that were present on the machine at all. The attackers retain access to the encryption keys and are essentially holding the organization’s data hostage until payment is received, or the organization ignores the request because they have full and accurate back-ups of all data. Typically, in these attacks, the storage on the machine is encrypted immediately, leaving the user with a screen that looks much like this:
What is the Attacker Looking to Gain?
In the case of a healthcare environment such as a hospital, this can be extremely challenging because there is no flexibility in the availability of these files. Healthcare providers must have them. There are times when the ability to access these documents is literally life or death. This forces the hand of the healthcare organization into paying the fee the attackers request. Many organizations have started to keep intermediary organizations to quickly initiate these payments in Bitcoin (which is what is typically used for these ransomware attacks).
The attackers in this case are extremely knowledgeable about the financial aspect of this type of attack, and they understand that the organizations that are targeted will likely not pay the ransom if it is too high. They have found a sweet spot in the amount of ransom to charge, and according to (Ponemon, 2017), that amount is $2,500. That is the amount that most companies are willing to pay in order to have their data decrypted and returned to the original state. In speaking specifically about healthcare organizations, this amount is tiny when thinking of the devastating effects that could come from not paying the attackers.
How to Protect your Organization’s Data
The first thing to do to ensure that your organization is protected from ransomware and most other types of attacks is to educate your employees about the importance of computer security and malicious links. Intelligent employees can identify and report suspicious emails to the proper authorities and ensure that there is no initial vector for the ransomware at all. Secondly, preparation is key in this situation. Preparing for the inevitable attack is the best mindset to have, and this can be in the form of mail filtering, proxies, and firewall rules. In the event that something does happen, all organizations should have a plan in place. Who do you call if you log into your computer at work and that ransomware screen pops up? There is nothing wrong with holding a tabletop exercise with your employees and walking through exactly what needs to happen. With an approach that encompasses these important aspects along with your local tactics and techniques, you can sleep well at night knowing that although you can never say that you’ve won the war, your organization has done its due diligence in preparing for the battle.
Author Bio
John Tagita Jr. is a Sr. Cybersecurity Engineer intern with Alpine Security. He holds a variety of industry certifications including CISSP, GIAC, GCFA, and CCFE. John has a passion for forensic investigations and breach response cases, application security, penetration testing, and blockchain technology. He holds degrees in Information Technology, Cyber Security, and Criminal Justice. John is currently active duty in the US Air Force service as a Cyberwarfare Training Chief.
When John is not working in the cyber security arena, you may find him developing Capture the Flag competitions, such as Hacktober or Hack The Arch, or competing himself. He also is passionate about security research and networking with other like-minded hackers. John loves spending the rest of his down-time with his beautiful wife and his four devilishly handsome sons.
Link up with John on social media at https://twitter.com/attackd0gz on Twitter, and https://www.linkedin.com/in/netsecspecialist on LinkedIn.