Cybercrime is not just the plotline of bad TV movies. It’s a $600 billion global business that accounts for 0.8% of the world’s GDP. Anyone on the internet – and there are 3.2 billion of us – is a potential victim.
While phishing scams and identity theft are old news, the more serious threats to organizations are ransomware and extortionware. In fact at Europol’s 2018 Internet Organized Crime Threat Assessment, the European crime prevention agency stated, “In a few short years, ransomware has become a staple attack tool for cybercriminals, rapidly accommodating aspects common to other successful malware such as affiliate programs and as-a-service business models.”
Ransomware’s sister threats are a different form of cybercrime called cyber blackmail or cyber extortion. Blackmail doesn’t necessarily involve sophisticated technology. But ransomware and cyber extortion typically do. While these two types of malware share common themes, they also differ in key respects. What’s the difference between ransomware and extortionware? And what can you do to prevent your company from becoming a victim of cybercrime.
What is Ransomware?
Ransomware is a type of malware that locks a computer system down until the victim pays the extortioner for the key code to unlock the device. It’s an obvious form of cybercrime. While some internet criminals try to fly below the surface, stealing data without you realizing it, ransomware is overt. The hacker is telling you in plain language, “We’ve encrypted your system. The key is in our lockbox. If you want your data or computer to work again, you’ll pay us.” Usually, the victim has to pay in Bitcoin or through another hard-to-trace method.
It’s the most common form of cybercrime and perhaps the most effective. Who wouldn’t pay a few hundred dollars to a criminal instead of a few thousand to a break-fix IT service, which might not be able to unlock the system anyway? The trouble is, there’s nothing to stop the criminal from coming back again … and again. Ransomware can cost a lot more than the initial payment; it also costs time, productivity, and reputation.
Examples of ransomware
The first ransomware appeared in 1989. Hackers mailed floppy disks (remember those?) to unsuspecting victims who inadvertently installed the malware on their computers. To get the key, the victim had to mail either $189 or $378 to Panama. Today’s cybercriminals operate a similar racket but with greater technical prowess. The WannaCry ransomware attack in 2017, which was linked to the North Korean government, infected about 200,000 computers in 150 countries.
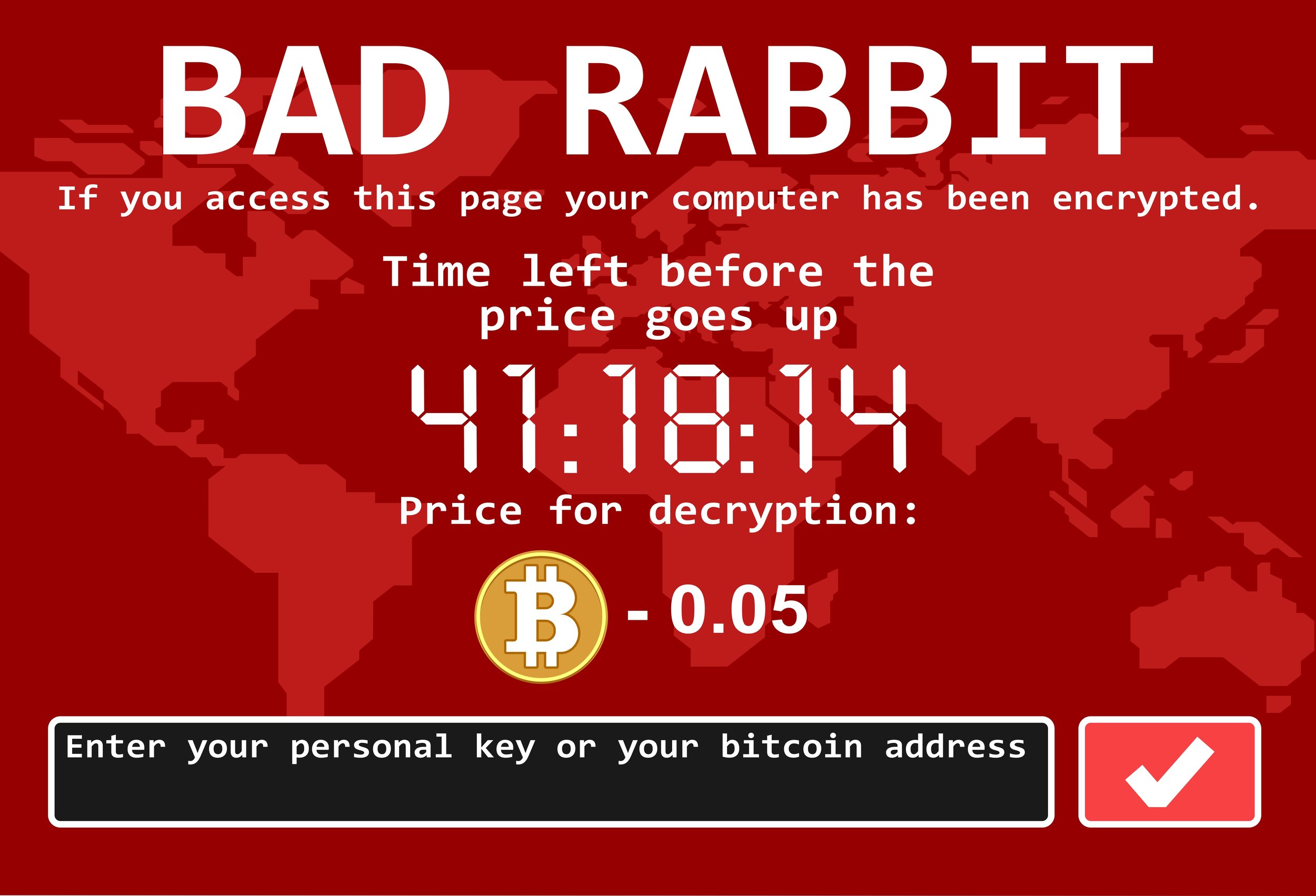
Bad Rabbit was ransomware that affected European and Russian users. Unlike WannaCry, which spread randomly, Bad Rabbit targeted its victims, which included the Odessa airport and Kiev’s mass transit system.
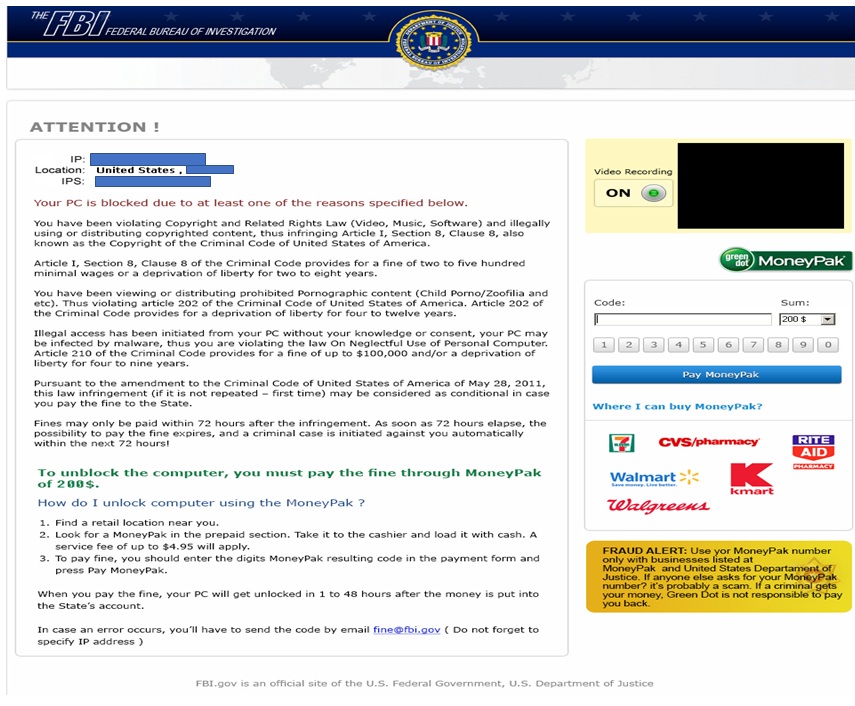
A relatively new and irritating form of ransomware is called “police-themed demands.” In this, the criminals claim to be the police who are shutting down your computer due to its use in a terrorist act or a child pornography ring. By paying a few hundred dollars in fines, the “police” claim, you can unlock your computer. Of course, the whole thing is bogus, and you’re the victim of ransomware.
What is cyber extortion?
Extortion is simply demanding a good, service, or payment to prevent violence or destruction of property. Some cybercriminals get ahead of the competition by demanding money before they hurt you. Much like the mobsters of yore who wanted payment for “security services,” these cyber extortionists basically tell you to pay them or they will lock up your system. According to Insureon, “Cyber extortionists may threaten to harm you, your reputation, or your property if you do not comply with their demands. Cyber extortion can take many forms.” For instance, a hacker may send malicious traffic using a bot, overwhelm the site with more requests than it can handle, or simply shut it down.
What is cyber blackmail?
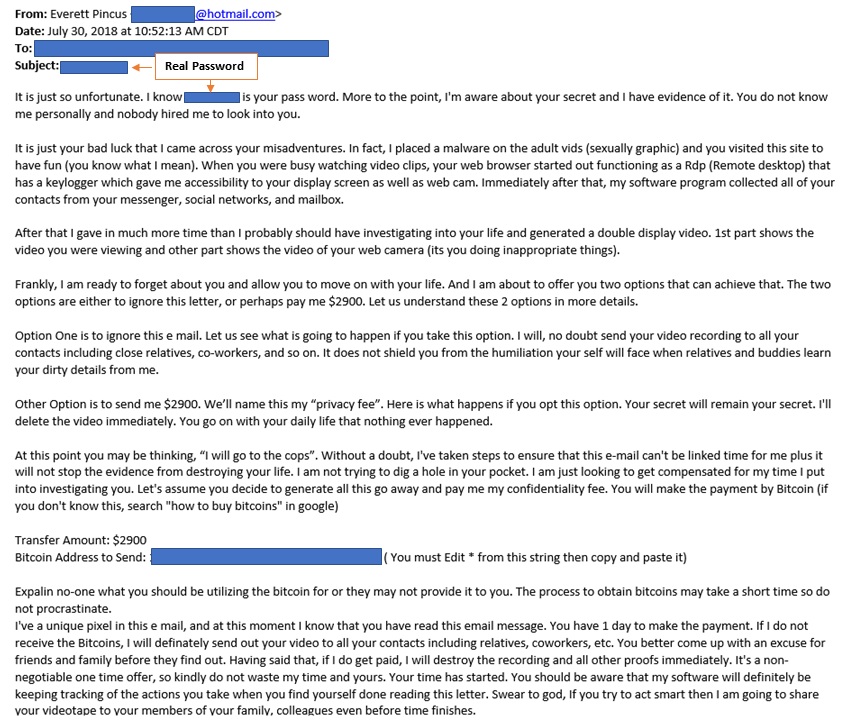
Blackmailers employ the psychology of fear and shame to motivate victims. In these cases, the cybercriminal will claim that he’s been inside your computer, snapped screenshots of embarrassing photos or searches, and recorded sketchy video using your camera. He will threaten to send the screenshots and pics to everyone in your address book or post them on social media unless you pay up. It’s basically cyber blackmail.
“Cyber-blackmail is the act of threatening to share information about a person to the public, their friends or family, unless a demand is met or money is paid,” according to the BBC. It is a particularly insidious kind of crime. In fact, some hackers are even targeting children.
Cyber blackmail doesn’t only affect individuals, but it also harms companies. Hackers claim they have stolen sensitive data from a company’s storage and threaten to expose it unless paid off. Many times, the hacker has no evidence at all and is simply bluffing. The really dangerous part is that emails from hackers often reveal they have secured your password, and while that may be all they have, it’s often enough to do some serious damage.
Am I a victim of ransomware, extortionware, or cyber blackmail?
Because these are forthright kinds of crime, you’ll likely know if you’re a victim. The hackers will tell you when they demand the ransom, threaten you for money, or want blackmail payoff. One handy way to assess the credibility of an extortion scheme or blackmail threat is at HaveIBeenPwned. This site lets you see what breaches your email address has been associated with, so you can determine if the password that is supposedly compromised and used for the cyber extortion or blackmail is simply from a previous breach or if the hacker really has broken into your system.
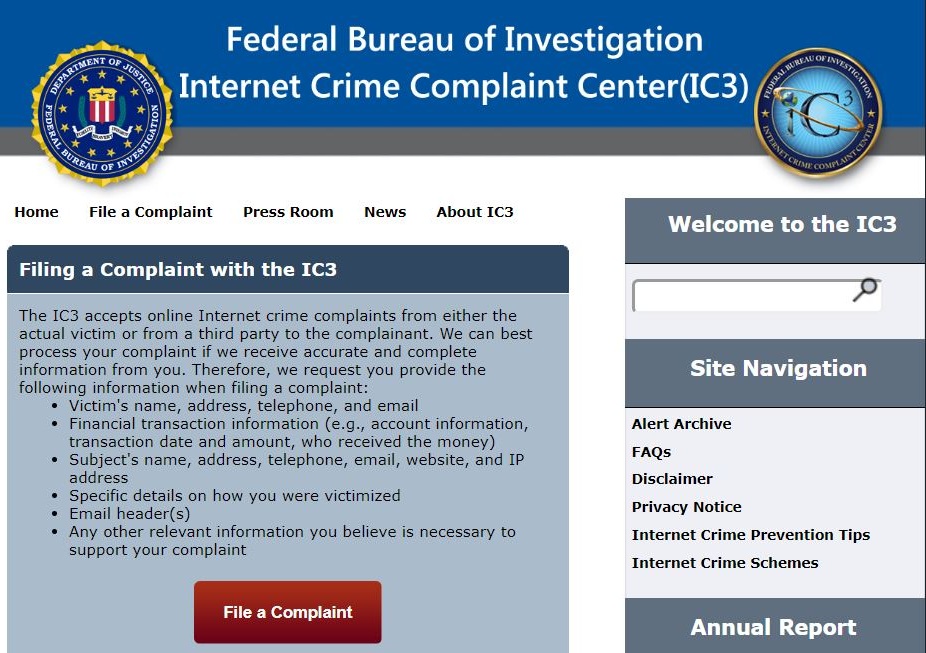
In no case should you pay off a cybercriminal even if you think they have something on you. A qualified cybersecurity services provider can help you determine the appropriate response and also protect you against future ransomware. Cyber blackmailers almost never have the goods on you they say they have, and extortionists are probably no match for your cybersecurity service provider or internal cybersecurity squad. Report cybercriminals to the FBI Internet Crime Complaint Center (IC3):
https://www.ic3.gov/default.aspx
How penetration testing and training can prevent cybercrime
At Alpine Security, our penetration testing services and training can help prevent both ransomware and extortionware. We can also help you know what to do if a hacker uses ransomware to lock down your systems. Penetration testing can help identify gaps in systems and networks, and our user awareness training, including our phishing services, can identify gaps in user training.
To learn more about protecting your organization from ransomware, cyber blackmail, and cyber extortion, or if you have an incident contact us today.