
The State of Ransomware 2020
...

...

...

...

...

...

...

...

Penetration testing offers two important benefits — security and regulatory compliance. Rising cybercrime, such as the Equifax breach, has affected millions of Americans who now insist on knowing that companies will keep their data secure. And government regulators are happy to help them do it by penalizing companies that do not comply with federal guidelines.
This blog is a walkthrough of digitalworld.local: BRAVERY. The VM was created by Donavan and you can download it from VulnHub. According to the author, it was originally designed for OSCP (Offensive Security Certified Professional) practice.

Anyone who is inspired to partake in a challenging course such as the Offensive Security Certified Professional (OSCP), or Licensed Penetration Tester-Master (LPT (Master)), knows that practice makes you a better hacker. Vulnhub is a great resource to find purpose-built virtual machine images to practice on. This image is based on a popular TV show, and we are going to walk through exploiting it together.
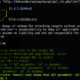
Hacking seemed like an arcane art, only mastered by those willing to spend years pouring over dusty tomes of x86 assembly language manuals and protocol RFCs. It did not occur to us that many of the vulnerabilities could be exploited by anyone with basic web development coding skills and the willingness to spend a few hours on research. One of these mysterious incantations was the dreaded “SQL Injection” attack. What exactly could one do with a SQL Injection attack, anyway? No one was quite sure, but since our software was going into a secure military installation, we were pretty sure that the perimeter defenses would prevent anyone from harming it.

Hacking humans with nanotechnology may sound like a concept from a futuristic science fiction novel or movie, but the truth is, it’s not that far off and it could be the next big cyberthreat. If you thought data breaches involving your social security number or credit card information were scary, imagine the ramifications nanotechnology hacking.

Penetration testing, also known as ethical hacking, is one of the hottest jobs in tech today. What other career lets you pretend you’re in The Matrix, working your way into systems like a top-level hacker, all without breaking any laws. Oh, and you’re getting paid for it.With a real-world penetration testing job, though, you’re not just playing at hacking into systems. You actually are hacking into systems, and your employer’s very existence may depend on your ability to do it.

Penetration testing, also known as pen testing, is an ethical hacking tactic that helps companies protect themselves. Penetration testers try to break into clients’ digital systems to find weaknesses before a black hat hacker does. This is a growing field as companies seek to prevent the high profile data breaches that have happened in recent years. The top penetration testing certifications can help you get into this field.

Web applications are the critical systems of many networks. They store, process, and transmit data. They are also vulnerable to hackers who can find vulnerabilities. So, the question becomes how secure is your network? And how comprehensively has it been tested?
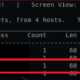
Byobu is a wonderful tool that allows multiple sessions running in the background, even when the SSH session that launched them dies.

Penetration testing – sometimes called white-hat hacking – is how companies manage risk, increase business continuity, and protect clients from data breaches. In highly regulated industries such as healthcare, banking, and service industries, it also helps companies stay compliant. SOC 2, HIPAA, and PCI DSS are three of the main regulations that require penetration testing.

Protecting your agency or company from cyber crime is critical to keeping your business running smoothly and profitably in the digital age.
What are two of the most likely areas of vulnerability in your cyber defense strategy

The purpose of this blog is to demonstrate how to brute force a login page using Burp Suite. There are other brute force tools such as Hydra and Ncrack. Although both are great tools, Burp Suite is more suitable for brute forcing a web application login page, whereas Hydra and Ncrack are more suitable for other protocols such as SSH and RDP.

This blog demonstrates how to download PowerShell Empire, a post-exploitation tool, in Kali Linux, create a script, make a connection back to your machine from the victim machine without Windows Defender blocking it, elevate privileges, and extract password hashes using Mimikatz. It is a versatile and useful tool that every penetration tester should have in their arsenal.
Interested in our cybersecurity training or services? Complete the form below and we’ll get back with you right away. We appreciate your interest.