Web applications are the critical systems of many networks. They store, process, and transmit data. They are also vulnerable to hackers who can find vulnerabilities. So, the question becomes how secure is your network? And how comprehensively has it been tested?
Web applications are the critical systems of many networks. They store, process, and transmit data. They are also vulnerable to hackers who can find vulnerabilities. So, the question becomes how secure is your network? And how comprehensively has it been tested?
To find these weaknesses before malicious hackers do, penetration testing is an essential tool. In web application penetration testing, an assessment of the security of the code and the use of software on which the applications run takes place. There are typically four main areas tested, per experts in the field:
- Injection vulnerabilities
- Broken authentication
- Broken authorization
- Improper error handling
Unfortunately, your programmers aren’t perfect. They will, on occasion, make errors in building your applications. A penetration test is like a check and balance for the work of your team but completed by an outside partner. Penetration testing is another safeguard to eradicate vulnerabilities to attacks. In compliance-related applications, penetration testing is required for PCI DSS and HIPAA. It is absolutely one of the best practices you can undertake to keep your network safe from hacking.
What Penetration Testing Could Have Prevented
Cyberattacks against web applications occur every day. Not all are thwarted but possibly could have been having penetration testing been carried out.
The Panama Papers breach made headlines in 2016, both for the data it revealed and the total disregard for securing web applications. The breach spread data about how certain wealthy individuals were able to offshore money in shell companies. The breach was made possible because of a vulnerable content management system plugin. If the plugin had been updated and secured, hackers would not have been apple to penetrate the application and breach the data.
The Equifax breach was also an incident that was totally preventable. Hackers entered the system through a web application vulnerability. The patch for the application was available but had not been updated. This was exploited to access the company’s Apache Struts web application, an enterprise platform that is used by many. Apache Struts refused blame with their VP Rene Gielen saying, “Most breaches we become aware of are caused by failure to update software components that are known to be vulnerable for months or even years.”
Vulnerability Assessments vs. Penetration Testing
Sometimes these terms are interchanged, but they are not the same. Vulnerability assessments are carried out to determine a list of vulnerabilities and prioritize those for review. Those organizations employing a vulnerability assessment are often aware they have security issues and need help identifying them. Review the differences between a pentest and vulnerability assessment here.
Penetration tests, however, are more comprehensive (and intrusive) than a vulnerability assessment and are designed to enact a specific hacking scenario. They are often used by companies that are confident in their security posture. Penetration testing assesses true risk. As an example, a vulnerability assessment will give you a list of vulnerable systems, independently, but a penetration test will give you the risk if an attack strung together minor-rated vulnerabilities from multiple systems to create an attack that resulted in a critical asset being compromised.
Three Types of Penetration Testing: Black Box, Gray Box, and White Box
In penetration testing, there are three main categories: black, gray, and white box. Each has a different approach and tests for different things.
Black Box Penetration Testing creates a scenario in which the ethical hacker has no knowledge of the system being attacked. The goal is to simulate external hacking. Black Box Test characteristics include unauthenticated access and no documentation other than IP address or URL.
Gray Box Penetration Testing assesses systems as an authenticated user with user-level access. This approach is used to test any insider threats on an application that supports multiple users to assess what kind of damage a user could do. The tester does not have access to the source code. With an authenticated profile, testers will attempt to escalate privileges or access controlled data. This testing ensures users cannot access sensitive data, such as another user’s information.
White Box Penetration Testing assesses a system with administrator or root-level access and knowledge. This knowledge can include architecture diagrams, design documents, specifications, and source code. This is the most comprehensive type of pentest. White Box Penetration Testing is typically used if you develop your own products or integrate systems into your environment.
OWASP Top 10
Beyond the three testing methods, there are specific web applications to test, including the OWASP (Open Web Application Security Project) Top 10. This a document that represents a broad consensus about the most critical security risks to web applications.
The 2017 Top 10 includes:
- Injection Flaws: SQL, NoSQL, OS and LDAP injection
- Broken Authentication: authentication can often be implemented incorrectly leaving passwords, keys or session tokens vulnerable
- Sensitive Data Exposure: checking for any weaknesses in the protection of sensitive data
- XML External Entities: these may disclose internal files, internal port scanning, remote code execution and denial of service attacks.
- Broken Access Control: test to ensure that rules and restrictions of authenticated users are upheld.
- Security Misconfiguration: this is a common issue resulting from insecure default configurations and a lack of patching and upgrading.
- Cross-Site Scripting (XSS): these flaws occur when applications include untrusted data without validating, leading to hijacking of sessions.
- Insecure Deserialization: this can lead to remote code execution.
- Using Components with Known Vulnerabilities: components have the same privileges as applications and need to be tested, too.
- Insufficient Logging and Monitoring: without proper logging and monitoring, breaches can go unnoticed.
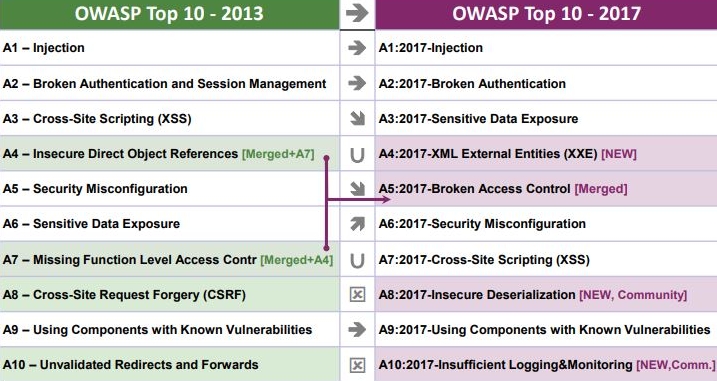
OWASP 2013 vs 2017 Top 10: Source: OWASP
Automated vs. Manual Testing
Parts of a penetration test, such as vulnerability identification, can be automated, but manual analysis and testing is critical. Automated testing tools offer many advantages like speed and wider coverage. However, not all penetration testing can be completed with automated tools. It takes a highly skilled analyst to perform manual testing. The manual approach is able to test for business logic vulnerabilities, which automated tools don’t understand. Automated tools won’t always have the most up-to-date knowledge when new vulnerabilities are released, thus manual testing will need to occur to find these. Automated tools also have a high false positive rate so manual testing is often used to validate these.
For the most effective penetration testing, there should be a combination of automated and manual testing. Automated testing has advantages, including less human resources required; however, manual testing is still critical as not everything can be detected through the automated process. Human testers often catch things that automated systems cannot.
Why You Need Third-Party Testing
While many organizations may complete internal penetration testing, it’s not as effective as a third-party. When your own team looks at their own code and applications, it’s not a fresh set of eyes. It’s like proofreading your own article. Your developers are typically experts in their domain and application, but they are not cybersecurity or pen testing experts. This is why you need specially trained professionals to carry out the pentest.
What to Look for in a Penetration Testing Partner
A penetration testing company uses techniques like those of cybercriminals in an attempt to find the vulnerabilities without going that step further and exposing data. Penetration testing is, of course, only as good as those carrying it out; here are some things to look for:
- Ensure the company’s testers have been screened with background checks and have all the right credentials, including CISSP, CSSLP, OSCP, ECSA, LPT(Master), and CEH.
- Ask what the testers do with the data and information that is found during the testing. This is your data so it needs to be secured. Find out how it’s stored and processed.
- Inquire about how the quality is warranted. You need to know the testers have been thorough so you should receive a full report, regardless of whether many things were found or nothing. You will feel even more assured with a partner that guarantees findings – or the test is free.
- Look for a partner that can expertly explain how to address vulnerabilities. You aren’t simply looking for a list. Your tester should have the experience and expertise to help you fix the problems.
- Seek an ongoing relationship where a provider can offer you advice on cybersecurity and what new threats are emerging. With a true partner, you can feel more confident about the future.
- Get details on their methodology and how they test systems. The seven overall phases of the methodology most employed are:
- Planning and Preparation
- Reconnaissance/Discovery
- Vulnerability Enumeration/Analysis
- Initial Exploitation
- Expanding Foothold/Deeper Penetration
- Cleanup
- Report Generation
Penetration Testing: Part of a Healthy Cybersecurity Risk Management Program
There are many tools used in cybersecurity. Robust programs try to address every possible situation. Penetration testing is one of the tools in your arsenal and the many benefits include:
- Determining weakness in the infrastructure, application, and people in order to develop controls
- Ensuring controls that have been implemented are effective, offering peace of mind to CISOs
- Spotting mistakes made by coders before hackers do
- Discovering new bugs in existing software and determining what updates can fix existing vulnerabilities
Working with Alpine Security for First-Class Penetration Testing
At Alpine Security, we are dedicated to providing thorough penetration testing, assessing all avenues of risk. We’ve helped numerous clients uncover issues in their applications so that they can be resolved. We deliver concise reports with prioritized action items. Our team includes experts with all the leading credentials in addition to experience with DoD penetration testing. Our services and deliverables include:
- Penetration Test Report
- Penetration Test Report Findings Review with your team via an online session
- Discounted Retest Option for a rerun of the Penetration Test after you fix identified problems
- Letter of Attestation
Alpine Security is here to help design a customized testing solution to keep your network safeguarded. Learn more about Alpine Security’s Penetration Testing services and how to get started today.