Email is such a seamless part of everyday life that it is easy to take for granted just how vulnerable anyone can be to a well-crafted effort to steal your identity or confidential financial information. One of the most effective methods used by hackers is phishing, which entails trying to trick you into clicking on a link or attachment in an email. Instead of the attachment, you thought you were opening, you have inadvertently opened the door to hacking from an outside source, usually without your knowledge.
Spotting Characteristics of Effective Phishing Emails
Phishing emails have specific characteristics based on standard tactics used by hackers to trick you into clicking. One of the most well-known phishing tactics involves spoofing the display name of an email. Because most email applications only show the display name and not the full address itself, many users will click without even looking at the actual email address the sender used. The address is often designed to look similar to a trusted email account, with only subtle differences such as switching two letters. Because most users are not expecting phishing emails from these fake accounts, a similar-looking address can easily go unnoticed by the recipient.
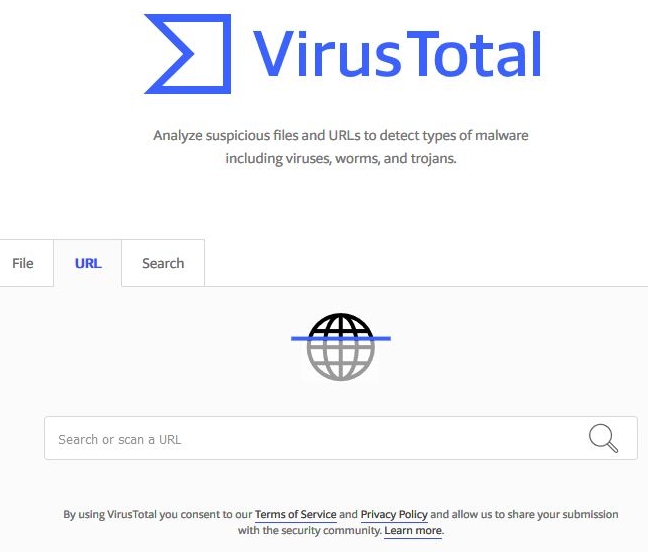
Check suspicious URLs with VirusTotal. Not a guarantee the URL is safe, but an indicator.
Another way to spot an effective phishing email is to move your mouse over any links embedded in the email. If the pop-up link address is from a site you do not recognize, do not click on the link. A better way to test suspicious links is to copy (do not click) the link and paste the link in the VirusTotal URL Checker (https://www.virustotal.com/#/home/url) to see if the URL is a known malicious link.
Other tells related to phishing emails are somewhat easier to catch. For example, if you see significant spelling mistakes or bad grammar, odds are the email is not from who you think it is from. Similarly, look for awkward language in the greeting of the email. Most companies you have accounts with will use your real name, not some nebulous greeting like “Dear Friend,” which can be a dead giveaway that the email you’re reading is not on the level.
Phishing emails often ask for your login and password information, which is something your real bank or other financial institutions would never ask for via email. Another common tactic is trying to scare you with threats that your account is frozen, prompting you to give up your personal information in response.
And most of all, do not click on or open attachments! Any link in a phishing email could contain malware or viruses that could wreak havoc on your computer by damaging your files, stealing your passwords, or spying on you without your knowledge.
Real-World Examples of Phishing
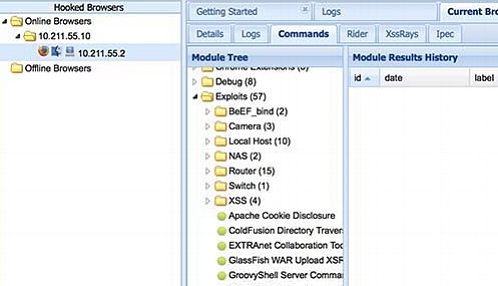
BeEF provides a GUI that allows you to easily control the target
A prime example of what can be done with phishing is the BeEF framework, which stands for The Browser Exploitation Framework. BeEF is a penetration testing tool focusing on the web browser. BeEF allows the professional penetration tester, or unethical hacker, to assess the exact security posture of a target environment by using client-side attack vectors.
BeEF is unique from other security frameworks as it measures the exploitability of the web browser. BeEF hooks one or more web browsers and uses them as a staging ground for launching directed command modules and additional attacks against the system from inside the browser context.
Can Phishing Training Tools Combat Phishing?
Phishing training tools do exist, but they typically use canned messages and, therefore, are not a realistic assessment. Even if an organization does phishing training, the training needs to be validated with a phishing test. At Alpine Security, we do realistic phishing campaigns explicitly tailored to the target. We are proud of our 100% success rate. Alpine emulates cybercriminals by using the same tactics and techniques they use to phish your users. Real criminals will not use canned messages delivered by your phishing testing platform. Validate the effectiveness of your phishing training with a realistic phishing test.
Phishing, Spear Phishing, and Whaling Explained
There are variations on the traditional phishing scam, some of which are narrowly focused and highly sophisticated. Spear phishing, for example, is a targeted attack directed towards a specific company, a group of employees, or even a particular person.
Whaling is even more sophisticated, targeting corporate executives at the highest levels by using their actual contact information to draft tailored emails in an attempt to gain illegal access. When the targeted user opens an attachment designed to emulate an official document, the user may be asked to install a plugin or some other seemingly innocuous software which could be designed to log all of the user’s keystrokes or some other malware.
Data Breaches with Phishing Hit Targets Small and Large
While many effective phishing email schemes target individual end-users, others result in large-scale data breaches. Even massive corporations with many layers of protection are not immune to these attacks.
The most prominent known data breach occurred in 2013 when unknown hackers compromised every single Yahoo user, for a total of three billion Yahoo accounts breached. The following year hackers hit eBay, managing to access encrypted passwords as well as other personal data associated with over 145 million accounts.
Another high-profile data breach took place in 2017 when the credit bureau Equifax was hacked, resulting in several hundred thousand stolen identities and endangering the data of over 143 Americans. Equifax was heavily criticized for not making the breach public until September 2017, which was four months after the system had been compromised. Hackers leveraged the Equifax breach to send people to a fake phishing website for credit monitoring.
Conclusion
Hacking with phishing is a serious problem that is not going away anytime soon. As long as black-hat hackers can market phishing as a service, the social engineering of peoples’ private and personal information will continue, and our records will never be truly secure. Phishing training tools are useful, but they need to be validated with a third-party phishing test.