Many organizations hear the term “malware” and immediately screech in fear. If you are interested in malware research, as long as you are using safe practices, there is not a lot to be afraid of. For those of you who are interested in malware research and figuring out how and why these pieces of malicious software do what they do, this article might be for you. We are going to talk about basic malware analysis. If you are interested in a safe place to grab actual examples of malware, check out the great repository Yuval Nativ has provided here:
https://github.com/ytisf/theZoo
I was speaking recently about how to start looking into malware samples safely. The way that always worked for me is to break the analysis into two different processes; static and dynamic. This article will go over the first of these steps. Once you are comfortable with static analysis, you should have enough data to compile some hypotheses about what the malware will do when executed, only then should you move into dynamic analysis and use that execution to affirm that hypothesis.
Static Analysis
Static analysis is looking at the file without ever executing it. There are different techniques that you can run against a malicious file to get an idea for what the file may do when executed.
The most important aspect of malware analysis is making sure that you are doing it safely. All of these actions that you are running against malicious files should be accomplished on a sandboxed VM with the NIC disabled. You do not want any accidental infections to occur, and being that all of the malware samples in The Zoo are live, it is extremely important to be careful.
Let’s say that you identify some anomalous activity from one of your workstations and you set out to capture some traffic from it. In the PCAP file, you are able to carve an EXE out and you want to rule it out as normal or malicious. The first thing that you can do is to upload the file to a platform VirusTotal which will leverage the power of the community to query whether or not anyone in the community has found this file malicious. You can also choose to search by the file hash if that is easier for you as well. In our case, I am going to use the EXE “procdump.exe” from the SysInternals Suite, which is a well-known executable, and is not malicious in any way.
After I drag and drop the file into VirusTotal’s UI, I am brought to this screen:
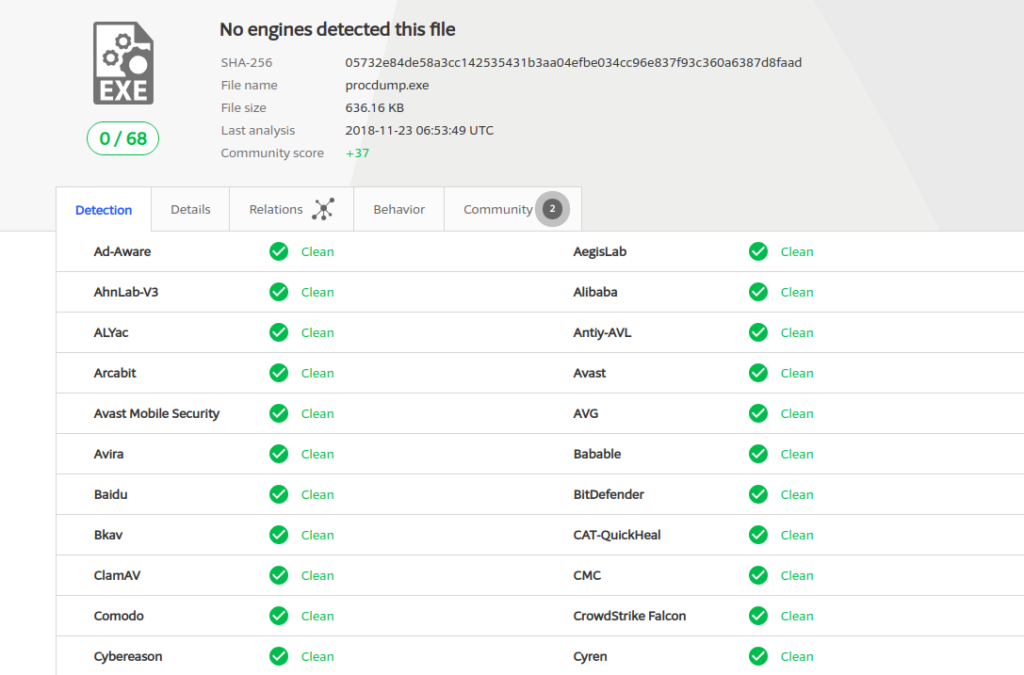
Virus Total UI screenshot
It is clear that no virus detection engines have deemed this file malicious, and more importantly, no one has reported it as malicious. The next thing that we can do for simple static analysis is to look at the strings for the file and see if there is anything glaringly obvious that would warrant a further look into the file.
Strings is a Linux utility that allows you to see the printable strings in a file. The help page looks like this:
Strings Linux Utility screenshot
When we run strings against the procdump.exe file, with a minimum character length of 15, this is the output that we get:
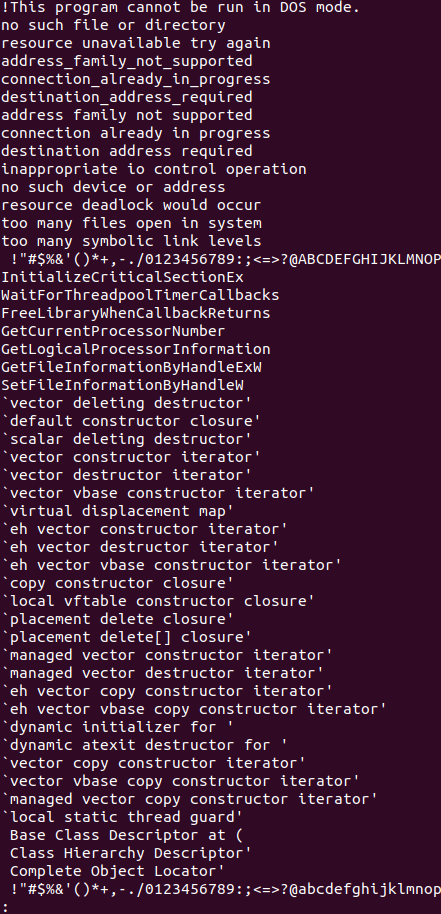
Strings Linux Utility output
With some familiarity into the code and experience in looking at actual malicious files in this same manner in the past, we are able to make a decision on whether or not to continue with our investigation, or move on to the next thread to start pulling. Depending on the maturity of your program, your next step might vary widely as to what to do next. You might choose from one of two actions: continue to statically research the executable until you are confident in your findings, or move on to dynamic analysis in running the executable in a sandbox.
In Part 2 of this article, we will cover dynamic analysis and how we can form hypotheses about the file based on our static analysis findings.
Learn more about Malware Analysis in our Intro to Malware Behavioral Analysis Course.

John Tagita Jr
Author Bio
John Tagita Jr. is a Sr. Cybersecurity Engineer intern with Alpine Security. He holds a variety of industry certifications including CISSP, GIAC, GCFA, and CCFE. John has a passion for forensic investigations and breach response cases, application security, penetration testing, and blockchain technology. He holds degrees in Information Technology, Cyber Security, and Criminal Justice. John is currently active duty in the US Air Force service as a Cyberwarfare Training Chief.
When John is not working in the cyber security arena, you may find him developing Capture the Flag competitions, such as Hacktober or Hack The Arch, or competing himself. He also is passionate about security research and networking with other like-minded hackers. John loves spending the rest of his down-time with his beautiful wife and his four devilishly handsome sons.
Link up with John on social media at https://twitter.com/attackd0gz on Twitter, and https://www.linkedin.com/in/netsecspecialist on LinkedIn.