Introduction

Unlike me, most normal people don’t spend much of their day marveling at the wonder of Public Key Cryptography. However, like readily-available food, clean water, gasoline, and other things we take for granted, anyone who uses the internet daily relies on Public Key Cryptography every time they check their email, send a chat message, login to their bank, buy something on the internet, or does a search on Google or YouTube. Public Key Cryptography is what makes privacy on the internet possible. It is the basis for End-to-End Encryption, which ensures that data is encrypted from the browser to the web-server, and (theoretically) not able to be read or modified by a third-party along the way.
In this blog post, we won’t be discussing theory or implementation details of Public Key Encryption. Rather, we are going to look at it from a practical perspective by answering the question, “How can I tell if someone is spying, or trying to spy, on my web browsing?”
That Little Lock Symbol
We’ll start by talking about “That Little Lock Symbol” that you see in the browser when you go to a website whose URL starts with https://. Let’s take YouTube for example.
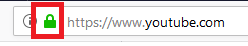 That Little Lock Symbol
That Little Lock Symbol
That Little Lock Symbol tells you that your connection to YouTube is secure. What that means is that as your traffic to and from YouTube traverses the internet, an attacker at one of the intermediate way-stations of your packets cannot read or modify the contents of those packets. So, although an attacker could see that you are browsing and watching videos on YouTube, they would not be able to tell what videos you are watching, or to redirect you to another website. In other words, Public Key Encryption provides confidentiality and integrity of your traffic until it reaches YouTube.
Now, let’s pretend that someone is attempting to spy on you by performing a Man-in-the-Middle (MitM) attack. The attacker manages to position himself between you and the website you wish to browse. In most cases, this is what you would see when you try to navigate to the attacker’s fake YouTube site:
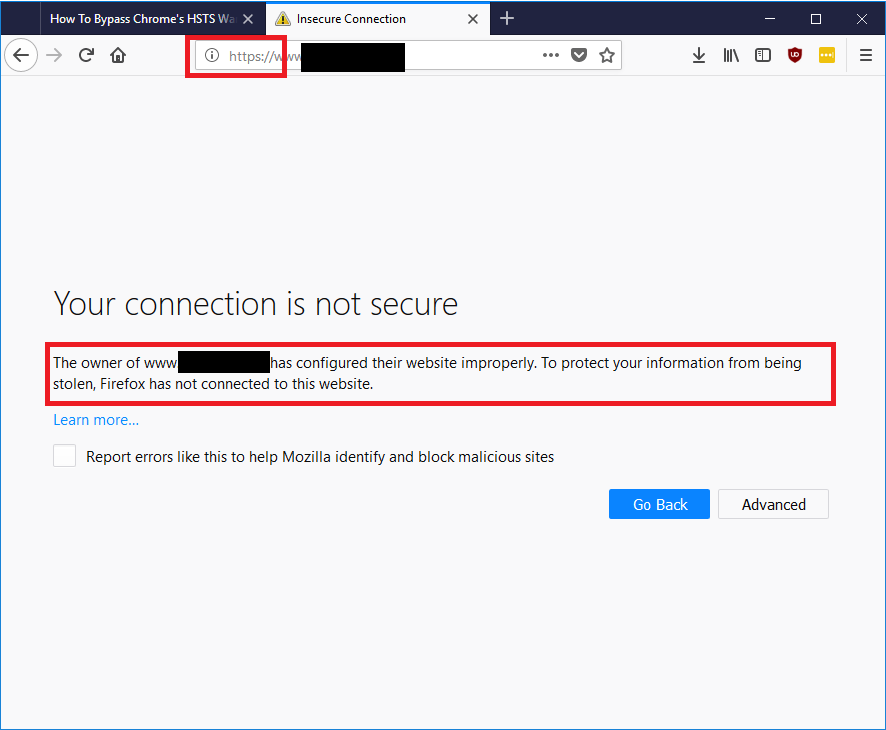 Warning About an Unsecure Connection
Warning About an Unsecure Connection
The browser warns you that there is something wrong with the Public Key Cryptography certificate of the site you are trying to navigate to. Over the last few years, browsers have made it more difficult to ignore the warning by adding layers of required steps that a user must take to ignore it.
If you do manage to circumvent the browser’s protection against invalid certificates, you will see something like this in Firefox (the other browsers will look somewhat different).
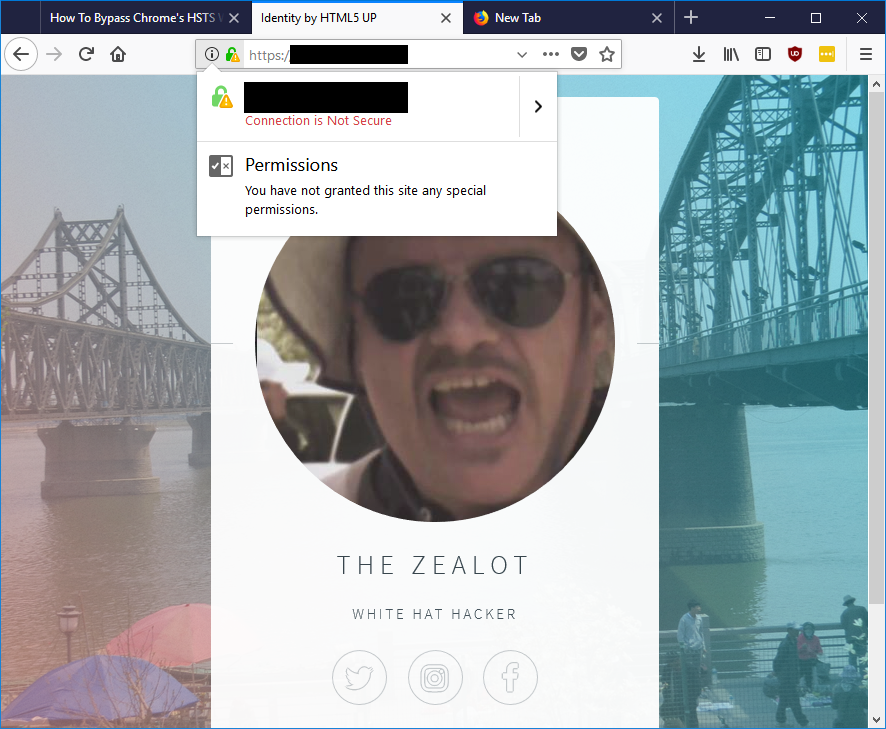 Warning That Connection Is Not Secure
Warning That Connection Is Not Secure
Notice the broken lock symbol, which tells you something is wrong with your certificate. This means that you cannot be guaranteed a private conversation between you and the web server.
Are You Being Spied On?
But what if the computer you are using is not under your complete control? Perhaps you are using a hotel lobby computer or a computer at your office. Is it possible for these computers to spy on your web sessions without your knowledge?
The answer is yes. Corporations can use SSL Inspection Platforms to strip the encryption from traffic so that it can be inspected for signs of viruses, infections, or intellectual property. They can do this because your browser implicitly trusts any certificate that has been digitally signed by any Certificate Authority (CA) that the browser trusts, or by any certificate that has been signed by any CA that has been signed by a CA, etc. To read encrypted traffic, your company may install an SSL Proxy, a computer that intercepts your computer’s request for an encrypted web page, makes the request for you, decrypts the traffic, inspects it, then re-encrypts it and sends it back to you. It can re-encrypt it and send it back to you, because your computer has had the SSL Proxy’s certificate installed on it, so it trusts it as a source of the encryption, without explicitly warning you.
So how can you know that this is being done? SSL Proxies can use the name of the organization that owns the page, and they can fake some other data related to the certificate, but what they can’t fake is the original website’s fingerprints. A website certificate fingerprint is a hash value that represents a digital signature performed by the Certificate Authority on the website certificate, guaranteeing that it belongs to the organization claiming it. To verify that a certificate is legitimate for a website, you can compare its fingerprints to those captured by a known good source.
To view the fingerprints of a website certificate (on Firefox, other browsers will be slightly different), click the Lock Symbol, followed by the arrow to the right of the website name.
 Viewing the Website Certificate Fingerprints, Part 1
Viewing the Website Certificate Fingerprints, Part 1
Then click More Information:
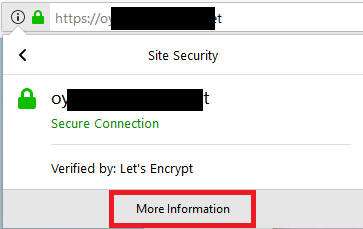 Viewing the Website Certificate Fingerprints, Part 2
Viewing the Website Certificate Fingerprints, Part 2
The Page Info window appears. Click View Certificate. Another window appears with certificate information, including the certificate fingerprints.
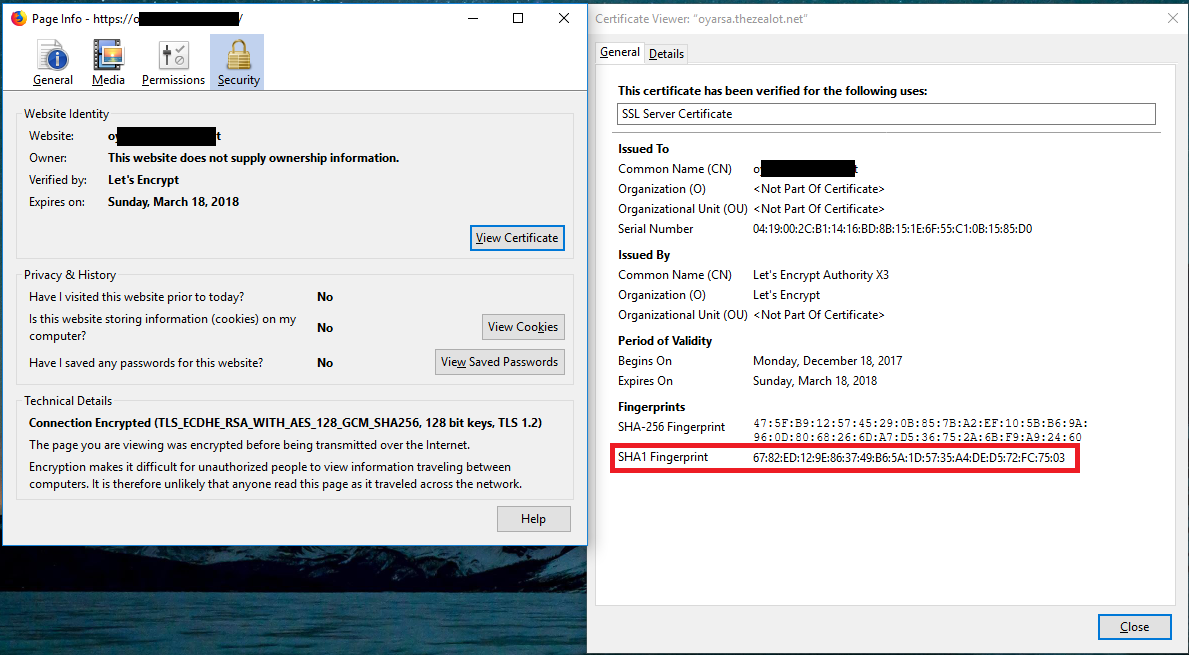 Viewing the Certificate Information, Including Fingerprints
Viewing the Certificate Information, Including Fingerprints
Stephen Gibson of Gibson Research Corporation fame has an excellent website to help you verify the validity of website certificates. GRC’s Fingerprints website presents the current certificate fingerprints for a few of the most commonly used websites, along with a field for you to submit any other website’s URL.
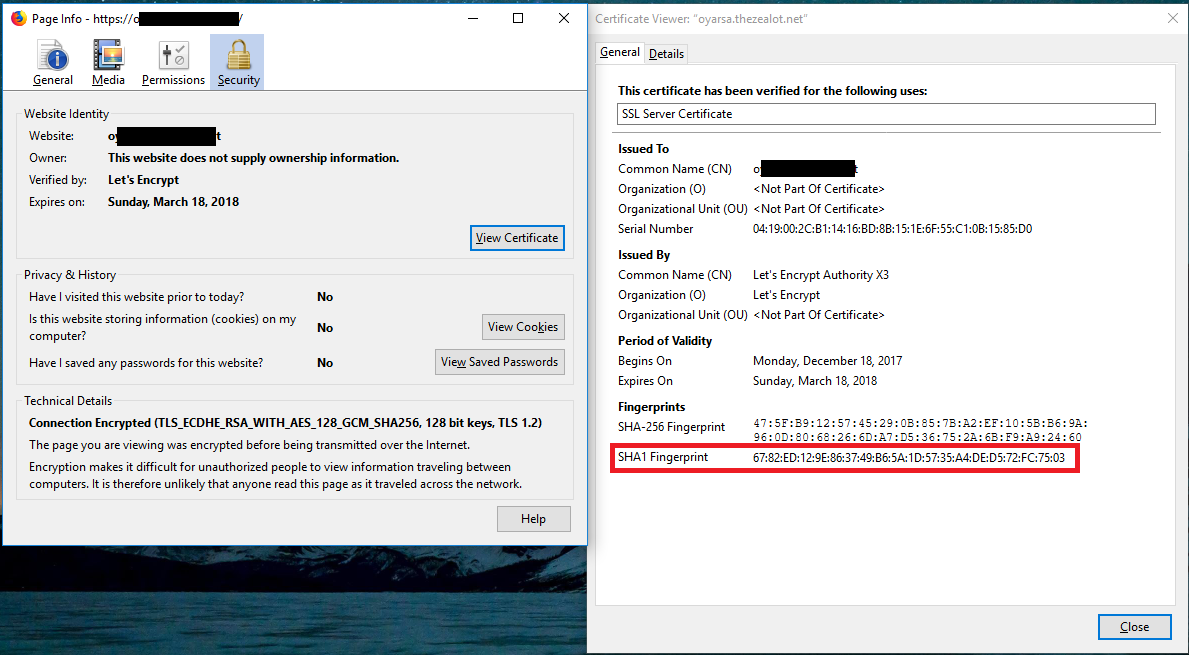 Gibson Research Corporation’s Fingerprints Website
Gibson Research Corporation’s Fingerprints Website
The Fingerprints website will independently verify the certificate fingerprints by visiting the website and presenting the fingerprints to you, so you can compare them against what your browser is reporting.
To verify a website’s certificate, enter its URL into the field in the Custom Site Fingerprinting text field, and click Fingerprint Site.
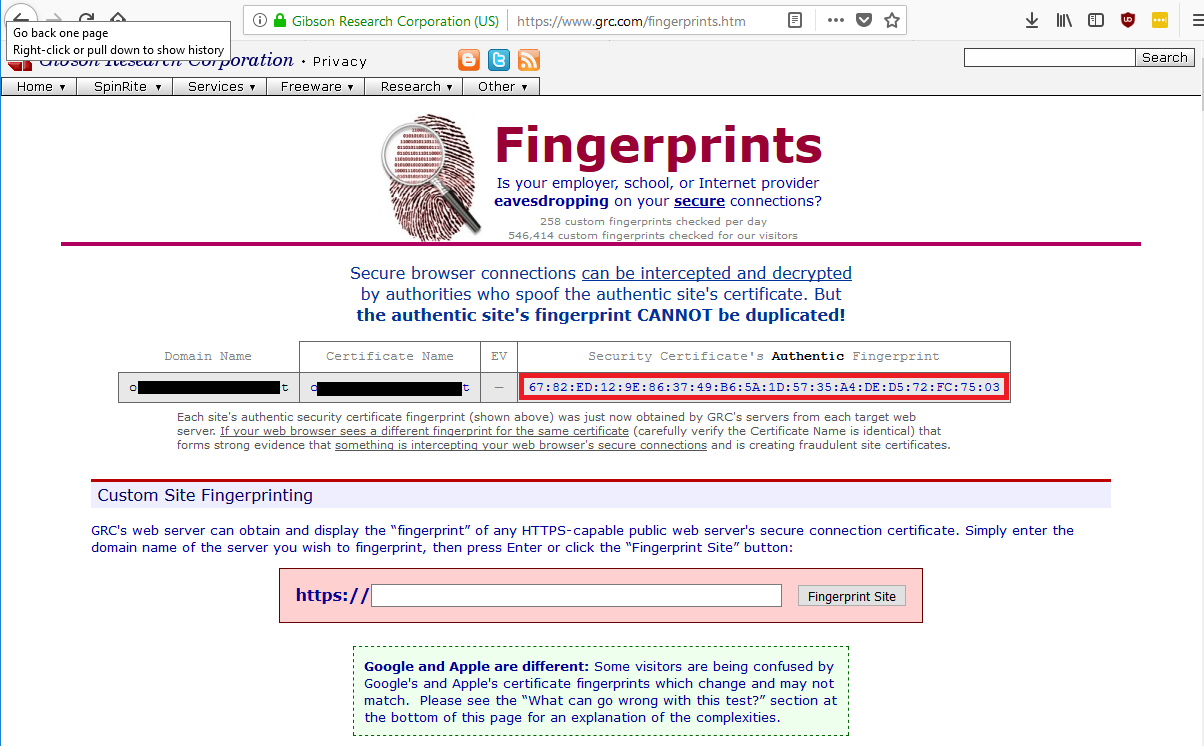 GRC’s Fingerprints Website Validates Website Certificate; Compare Fingerprint with That from the Website in Question
GRC’s Fingerprints Website Validates Website Certificate; Compare Fingerprint with That from the Website in Question
Since we can see that the fingerprint from GRC Fingerprints matches that shown by the browser, we can be sure that this website’s certificate is authentic, and our traffic is encrypted to it. We can also see that the network that we are using is not intercepting and decrypting the traffic going to it. Now, this does not necessarily mean that no decrypting is happening for other sites. It only means that it isn’t happening for this particular website.
GRC’s Fingerprints website gives detail on how all this works. It explains why this method may not work for some companies that have many different certificates distributed across many servers. Finally Fingerprints also explains other possible reasons for certificate fingerprints that don’t match.
Some Safe Browsing Advice
So now you know how to tell if a company is using network-based decryption to inspect traffic to your work, hotel, or school computer. As GRC Fingerprints explains, it will not necessarily tell you if your browsing is being monitored at the host level by spyware or other host-based monitoring software. Therefore, I recommend that you do not use a computer that is not under your complete control to do things like login to your sensitive personal accounts, such as Facebook or your bank. If you want to check these websites at work, use your cell phone or a device tethered to your phone, such as a tablet or a Chromebook to do so.
Author Bio
 Doc Sewell in Dandong, China, across the Yalu River from Shinuiju, North Korea
Doc Sewell in Dandong, China, across the Yalu River from Shinuiju, North Korea
Daniel “Doc” Sewell is the CTO and a Trainer for Alpine Security. He currently holds many security-related certifications, including EC-Council Certified Security Analyst (ECSA), Licensed Penetration Tester (Master), Offensive Security Certified Professional (OSCP), Certified Information Systems Security Professional (CISSP) and Certified Secure Software Lifecycle Professional (CSSLP). Doc has many years of experience in software development, working on web interfaces, database applications, thick-client GUIs, battlefield simulation software, automated aircraft scheduling systems, embedded systems, and multi-threaded CPU and GPU applications. Doc’s cybersecurity experience includes penetration testing a fighter jet embedded system, penetration testing medical lab devices, creating phishing emails and fake web sites for social engineering engagements, and teaching security courses to world-renowned organizations such as Lockheed Martin and the Hong Kong Police Department. Doc’s hobbies and interests include home networking, operating systems, computer gaming, reading, movie watching, and traveling.




