A few months ago, I took and passed EC Council’s Licensed Penetration Tester (Master) [a.k.a. “LPT (Master)”] examination. It was a five-day, hands-on exam that required me to complete a simulated penetration test in the iLabs online environment. I then had to complete a full penetration test report, detailing the vulnerabilities, exploits, and required remediations for the customer’s network and systems.
After successfully completing the examination, I was invited to join the LPT Advisory Board by EC-Council. As a member of the board, I was offered a chance to be one of the first people in the world to test out the new, upcoming LPT (Master) exam. Because of my work schedule, I was not able to actually test drive the new exam until after it was announced at Hacker Halted 2017 by EC Council’s President, Jay Bavisi.
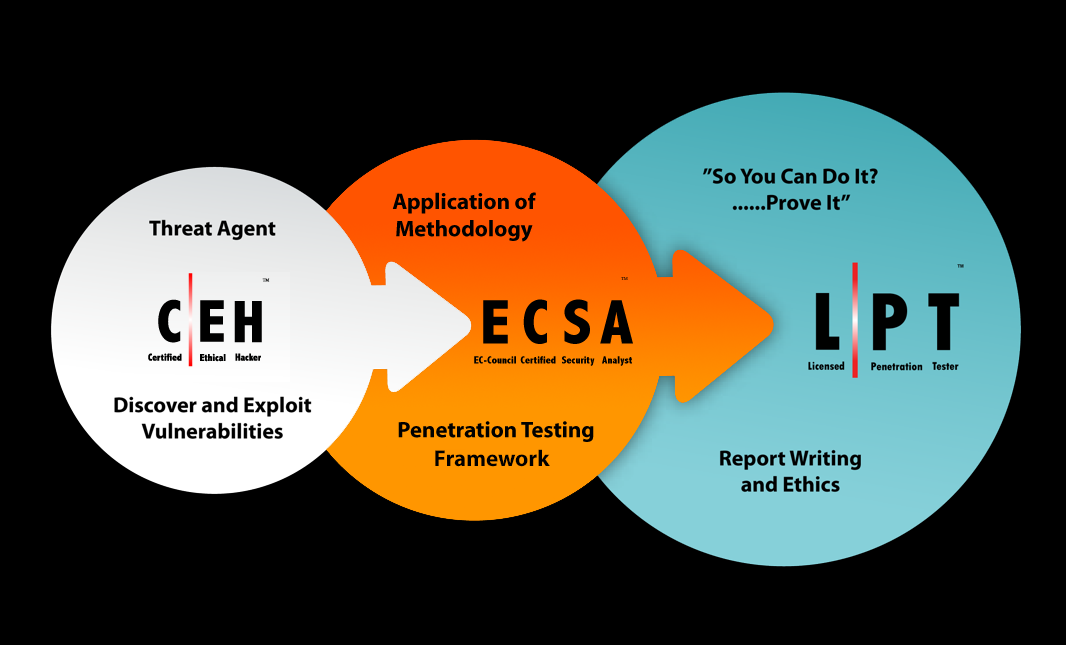 The EC Council Learning Track: Knowledge (CEH), Skill (ECSA), Ability (LPT Master)
The EC Council Learning Track: Knowledge (CEH), Skill (ECSA), Ability (LPT Master)
The previous hands-on exam took place in a single session over a five-day period. Once you started the exam, the clock started, and you had to complete the entire exam in five days. You then had 25 more days to complete and submit the LPT (Master) penetration test report.
The most significant difference with the new exam format is that it is proctored. This means that you are being watched over your webcam for the entire period of the session. Proctoring a five-day exam is impractical, so the exam was split into three six-hour sessions. Each six-hour session consists of three individual “challenges”. Each challenge involves recovering the contents of a secret file, but some challenges will require hacking more than one machine. You enter the contents of the file into a web page and submit it when you are done with the session. You must complete at least one challenge per session, and you must complete at least five out of the nine sessions to pass the exam. If you successfully pass the hands-on portion, you are then required to submit your written pentest report within a certain time period (as I recall, you have 45 days to complete the entire process).
I was finally able to schedule the exam for October 18th, 23rd, and 25th of 2017. I had originally scheduled it for Oct 18-20, but I was later informed that there must be at least two days between sessions. This was even though the scheduling website allowed me to schedule the test for three days in a row.
I believe the test was proctored out of the Eastern Hemisphere because I had the choice of either scheduling my sessions to start at 12:00 midnight, or 6:00 AM, Central Daylight Time. I chose to schedule all my sessions to start at 6:00 AM. Once scheduled, you have a fifteen-minute grace period to get logged in and connected to the proctors. If you fail to connect within the grace period, you must reschedule that session. Because of some technical difficulties, on my end or theirs, my final session nearly went over the limit; I got signed in about two minutes before the fifteen minutes expired. Before being allowed to take the exam, you have to prove your identity with a government-issued identification. Once you start a session, you are allowed to take two five-minute breaks away from the web camera. You will definitely want to keep that in mind when deciding how much coffee / soda / energy drink to imbibe before the test! You are allowed to stand and stretch within view of the camera, if you need to. The proctors can see and hear everything you are doing, and they monitor the chat window. So, if you need assistance, they are very responsive.
Having only six hours to hack three (or more) computers adds to the difficulty and the stress level, over the leisurely pace of the previous five-day exam. You must stay much more focused on your methodology and process, because it is easy to chase bunnies down their holes if you are not paying attention to the time. Also, since each session is essentially stand-alone, it is imperative that you grab all the screenshots you are going to need for your report while you are doing the test. If you miss one, that’s it. You won’t have time (like I did in the five-day exam) to go back and grab them after the fact. On the first LPT (Master) exam, I started working on the report before my five days were up, and so I could go back and retry each of the exploits to make sure that I had not missed any screenshots. During this exam, I was much more focused on making sure I got to each of the machines. I did miss a couple of screenshots that would have added some value to my report. One important piece of advice: don’t forget to take screenshots of your important nmap scans! Those will be important for your pentest report later.
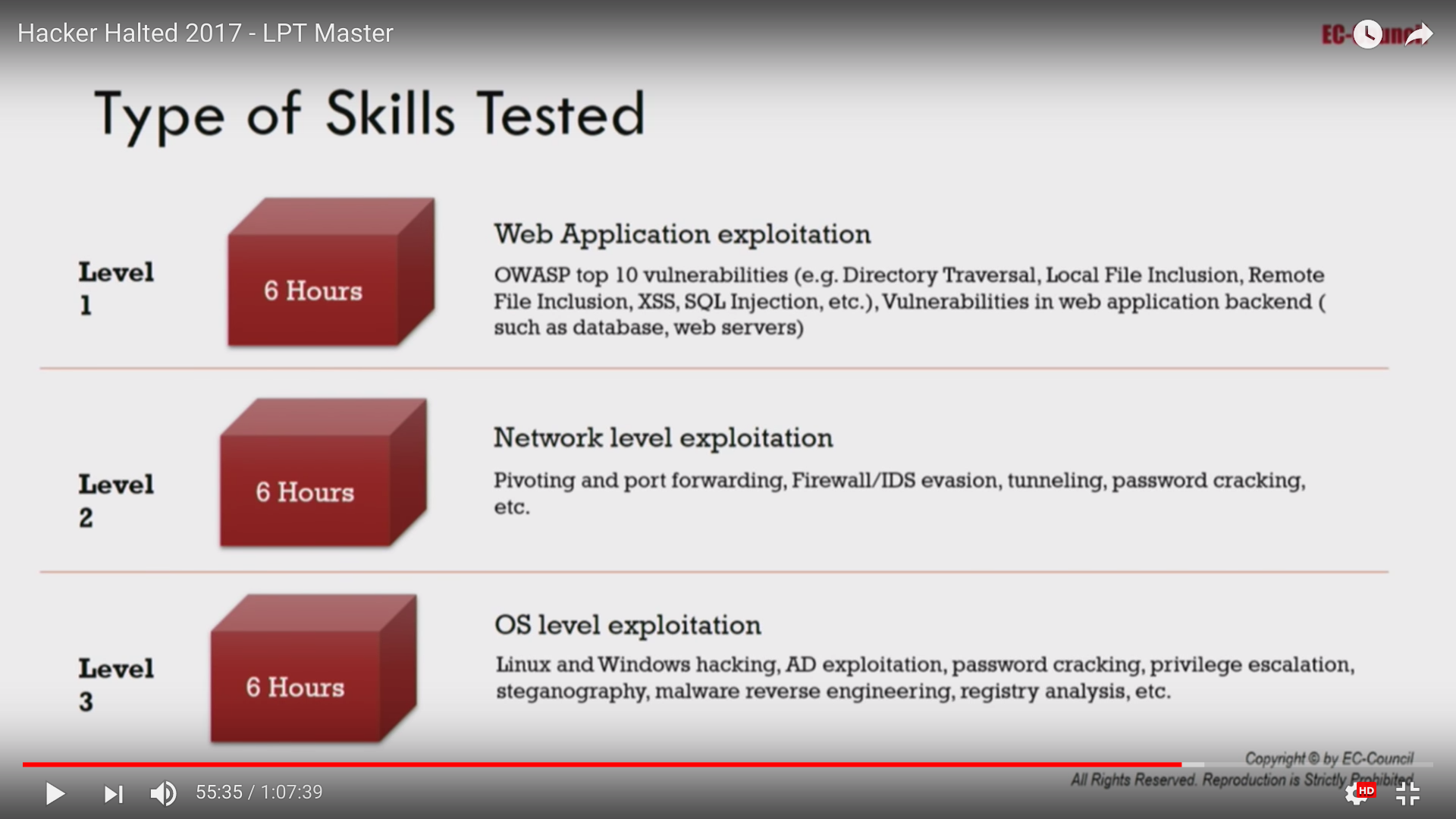 Skills Tested in Each of the Three Sessions (from EC Council President Jay Bavisi’s Presentation at Hacker Halted, 2017)
Skills Tested in Each of the Three Sessions (from EC Council President Jay Bavisi’s Presentation at Hacker Halted, 2017)
As I wrote in my previous piece, OSCP vs LPT (Master): A Comparison Made by a Cybersecurity Professional with Both Certifications, the OSCP and the LPT (Master) focus on different areas. The OSCP focuses on hard-core hacking skills, while the LPT (Master) focuses on a repeatable methodology for conducting a pentest. That is still true. However, the LPT (Master) has “upped its game”. It now covers more of the “hard core” skills, such as tweaking custom exploits (such as ones from Exploit DB), pivoting, password cracking, etc. The difficulty of the test has increased dramatically, and not just because of the time limit. Unlike the previous test, where I completed all the LPT (Master) challenges within the five-day period, this time, I was only able to complete seven out of the nine challenges. I got all three challenges in the first session, but only two in the second, and two in the third. I probably only needed fifteen more minutes in Session 2 to complete the third challenge, but another couple of hours to complete the last challenge in Session 3. I ran into the same problem that I did when taking the OSCP test. The time limit adds to the pressure, and it makes it easy for you to waste time “chasing bunnies”. You also don’t get the luxury of “walking away” from the exam, going off to exercise, take a shower, take a nap, watch TV or play a video game, to take your mind off the problem for a while. That helped me tremendously on my first LPT (Master) exam. I could come to the exam after a full night’s sleep and approach problems from a whole new angle. I was under much more pressure, and I was required to keep focus on the pentesting process and methodology as a whole. Keeping good documentation and screenshots was even more critical, since I did not have the ability to revisit a session once it was completed.
Despite being more difficult, the new LPT (Master) format has a few primary benefits. Since it is now three six-hour sessions that can be scheduled independently, it should be easier for more people to take it. It is not always easy to take five days away from work and family life to take an exam. Also, if you don’t pass a session, you are done. There is no need to take the others, file the report, and wait for the results. You know immediately that you must go back and practice some more. Finally, being the world’s first (and only) proctored, hands-on penetration testing exam, the LPT (Master) should have unmatched credibility with the industry. Whenever an endeavor has a large payoff (as it does for cybersecurity professionals), there is the temptation for some unscrupulous people to try to short-circuit the process… in other words, cheat. The new LPT (Master), being proctored, makes it nearly impossible to cheat on the exam. Organizations looking to hire those with the new LPT (Master) exam will know that it was really the individual who took and passed the exam.
After submitting my report on EC Council’s Aspen website, I was presented with a message that it would take up to seven days to grade the report. I received an email in about three days that said my report was accepted, which means I passed the exam.
In summary, I found the new proctored LPT (Master) exam to be a good bit more difficult than the previous version. The time limit, although making scheduling the exam easier, adds pressure. This can be a good thing, however, in that it makes you focus even more on methodology. Enumeration is of critical importance here. As far as the proctoring goes, it felt strange being “watched” during the examination. I tend to mutter out loud to myself while I am working, as I find it helps me think. I hope I wasn’t too much of a source of amusement to the proctors! The proctors and technical team were readily available to quickly help me with a couple of technical issues that I experienced. As the world’s first proctored hands-on pentesting exam, the new LPT (Master) will address any issues of exam credibility. Finally, there were some much more difficult challenges in this version as well, adding more focus on some of those “hard-core hacking skills” that the OSCP emphasizes, bringing it closer to the OSCP in “technical difficulty”. If you have your ECSA and / or OSCP, I definitely recommend adding LPT (Master) to your list of certifications to demonstrate your ability to conduct a penetration test while following a proven methodology.
To learn more about the new proctored LPT (Master) Exam, click here.
Author Bio
 Doc Sewell in Dandong, China, across the Yalu River from Shinuiju, North Korea
Doc Sewell in Dandong, China, across the Yalu River from Shinuiju, North Korea
Daniel “Doc” Sewell is the Lead Cybersecurity Engineer and Trainer for Alpine Security. He currently holds many security-related certifications, including EC-Council Certified Security Analyst (ECSA), Licensed Penetration Tester (Master), Offensive Security Certified Professional (OSCP), Certified Information Systems Security Professional (CISSP) and Certified Secure Software Lifecycle Professional (CSSLP). Doc has many years of experience in software development, working on web interfaces, database applications, thick-client GUIs, battlefield simulation software, automated aircraft scheduling systems, embedded systems, and multi-threaded CPU and GPU applications. Doc’s cybersecurity experience includes penetration testing a fighter jet embedded system, penetration testing medical lab devices, creating phishing emails and fake web sites for social engineering engagements, and teaching security courses to world-renowned organizations such as Lockheed Martin and the Hong Kong Police Department. Doc’s hobbies and interests include home networking, operating systems, computer gaming, reading, movie watching, and traveling.