 The CIS Critical Controls were developed as a framework to not only ensure the successful realization of basic cybersecurity hygiene, but to lead to the planning and implementation of a robust security protocol. To build any cybersecurity protection schemata, it is necessary to know the extent of what it is you are protecting. This is the stated purpose of Control 1.
The CIS Critical Controls were developed as a framework to not only ensure the successful realization of basic cybersecurity hygiene, but to lead to the planning and implementation of a robust security protocol. To build any cybersecurity protection schemata, it is necessary to know the extent of what it is you are protecting. This is the stated purpose of Control 1.
CIS Control 1 Overview: Inventory of Authorized and Unauthorized Devices
Critical Control 1 states: “Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access” (CISv.7). This control is not so much intended to prevent unauthorized access, although a complete inventory with attendant policy enforcement will do just that. Instead, it is devised so an organization may be certain of what devices are on the network, so they may be effectively defended. Then these devices will not be the unknown gap in the defensive perimeter that allows a devastating attack to execute on an unsuspecting network. Compiling a detailed asset inventory may seem like an intimidating task for an organization of any size, especially if this is a first-time endeavor. However, Control 1 is segmented into eight subcontrols designed to give form to the mission at hand.
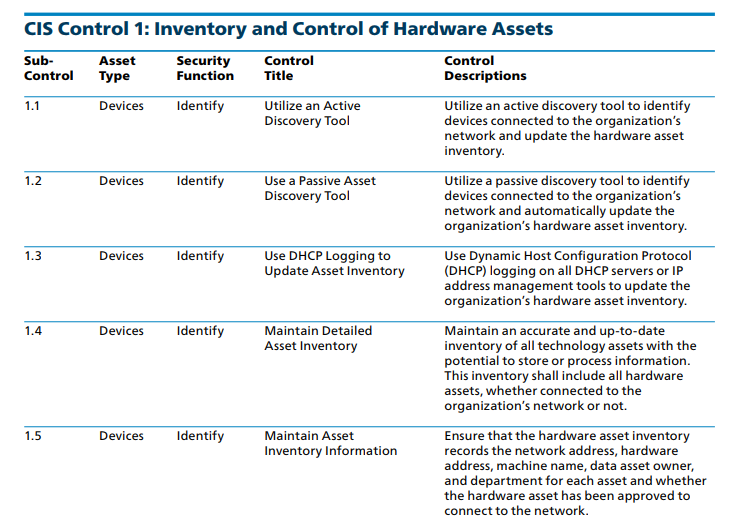
CIS Control 1 Subcontrols 1.1 – 1.5
CIS Control 1 Subcontrols
Subcontrols 1.1 and 1.2 recommend the use of both active and passive automated tools to identify device assets so they may be updated as needed and added to the hardware asset inventory. Anything with an IP address must be counted. This includes printers, copy machines, and even automated vending machines if they connect to the network. This asset inventory is also not limited to what is always attached to the network. Virtual Private Networks (VPNs) and mobile devices must also be inventoried, and these types of connections typically come and go on a network. Whether physical or virtual, if it has an IP address and ever connects to the network, it should be included as an asset. There are many such tools at varying price points, so that an organization will typically be able to devise a method that both works within their current framework and is financially feasible as well.
Subcontrol 1.3 advises Dynamic Host Configuration Protocol (DHCP) to be used to assign IP addresses. This automates IP allocation and is no small part of an IP address management system that aids in updating the hardware asset inventory and helps keep it updated. Subcontrols 1.4 and 1.5 focus on the maintenance of a detailed hardware asset inventory, whether or not the device is connected and whether or not the device is authorized to be connected. An inventory should at least indicate if an asset is portable, the name of the device, and the IP number. Including MAC addresses and serial numbers is a good practice to start with and maintain and can also be used to prove ownership for insurance purposes. Whatever information an organization deems necessary to keep in the asset inventory, it must be noted that this procedure is dynamic and ongoing for the lifecycle of any device. Records must also be kept of devices as they are deprecated and removed from the network or recommissioned and returned to the network. This is a priority on par with keeping updated blueprints and maintenance information for an organization’s physical and logical topology.
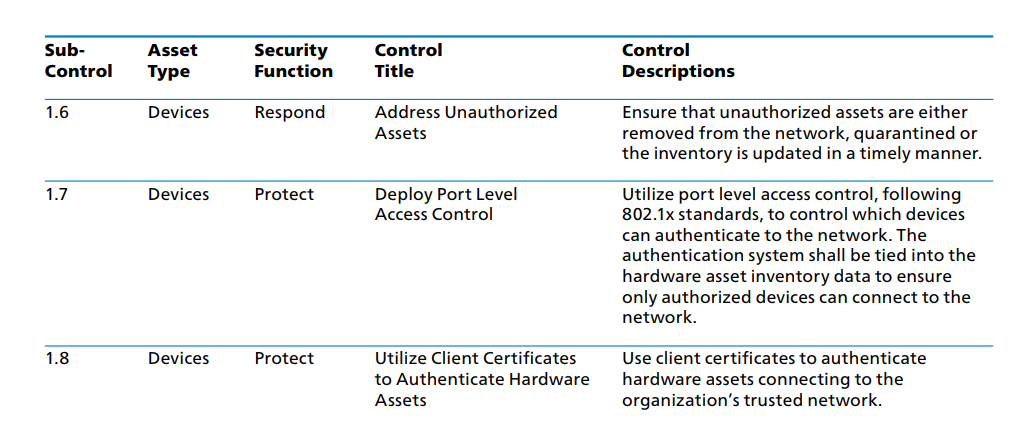
CIS Control 1 Subcontrols 1.6 – 1.8
Subcontrol 1.6 suggests steps to take in dealing with unauthorized devices. When an organization obtains the actual number of unauthorized devices currently connected to their network, they may also discover the need to update current policies and procedures for IoT (Internet of Things) devices. Such policies and procedures may take the form of employee education of various types, as well as clearly delineated employee agreements as to what is, and is not allowed on the network. ATP (Advanced Persistent Threats) and other hackers wait on the internet for such unauthorized devices to gain an entry point into a network, or to use as a pivot point if the network is already compromised. It is unfortunate but true that attack avenues are always evolving, and one of the most commonly used avenues of malware delivery is via email spear-phishing campaigns aimed at the unwary employee, or through the connection of an unauthorized and unprotected device such as a smart phone or laptop.
Once this inventory is complete, subcontrols 1.7 and 1.8 mention steps to take towards ensuring company control of which devices are authorized to connect to the network. Port-level controls are a necessity, along with proper switch configurations, and both should be tied to the device asset inventory. This should help ensure only authorized devices may connect to the network.
Certainly this is a task that requires time, attention to detail, and commitment. It is not as exciting as other defensive processes, but proper implementation will lead to the best execution of the other 19 Controls, as well as add to the overall improvement of an organization’s defense posture by increasing efficiency and response time and reducing the network attack surface.
Conclusion and Next Steps
The CIS Critical Controls are not rigid, but may be implemented in the ways that best suit an organization’s needs and acceptable risk. Neither are the CIS Critical Controls weighted equally. Critical Control 1 is as important and essential to the support of any cybersecurity posture as a foundation is to the support of a house. A variety of studies show that CIS Control implementation is proven to prevent around 90% of network attacks. That renders the return on investment undeniable, and the importance cannot be overstated to management and board members.
Alpine Security remains committed to fostering cybersecurity awareness globally and locally while providing our specialized services to organizations and individuals alike. Pursuant to that commitment, Alpine Security offers a free consultation on our Enterprise Security Audit (ESA) Service.
The ESA is based on the Top 20 Critical Controls published by the Center for Internet Security. The ESA is intended to provide a comprehensive picture of where an organization currently falls in Critical Control Implementation, while also delineating a roadmap for full implementation. With the increase in variety and methods of attack on organizations of all sizes and types, defensive uncertainty is a luxury no security-conscious entity can afford.
Author Bio

Mary, striking a Yoga Tree Pose
Mary Thierry is a Cybersecurity Specialist and Office Manager with Alpine Security. She is earning her Master’s Degree in Cybersecurity from Maryville University in Missouri. Mary was raised in rural Illinois on a farm, in a small town with 500 people in it. If you ask her nicely, Mary will tell you how to start heavy machinery on a cold morning, the best types of fertilizer, and the best places to build a deer stand. Earlier in her career, Mary taught special education, and then worked as a higher education facilitator for disadvantaged teens. Mary has a disabled daughter and is an advocate for persons with disabilities. Outside work, Mary loves to spend time with her family, bake, read Science Fiction/Horror, and attend Yoga classes.

