This is Part One of a Two-Part Series on Password Cracking.
Introduction
Application authentication that only requires a login and password is inherently unsecure, because an attacker only needs to obtain “one factor” to masquerade as a legitimate user. Often it is easy to guess legitimate login ids by doing some reconnaissance on the target of the attack. Many companies will re-use employee’s email ids (without the domain name) as a universal login for other systems in the company. Email addresses can be discovered from many online sources.
Additionally, users will often use unsecure passwords, because they are easier to remember. A company will often dictate rules for password complexity, but users will still tend to follow those rules in such a way that their passwords will be easier for them to remember. This predictability can make it easier for attackers to “guess” a legitimate user’s password.
System administrators and penetration testers can use Online Password Cracking tools to test their systems to look for users who are using weak passwords. Keep in mind that these tools should only be used on systems for which the user has owner permission. Breaking this rule is a felony in most jurisdictions.
What is “Online Password Cracking?”
Online password cracking is attacking a computer system through an interface that it presents to its legitimate users by attempting to guess the login credentials. For instance, an attacker can try to guess a user’s credentials for a web application login page; for an SSH or Telnet server; or for a network service such as Lightweight Directory Access Protocol (LDAP), one of the mail protocols (SMTP, POP3, or IMAP), FTP, or one of many others.
The tools that we discuss below generally support two modes: Dictionary and Brute Force. A Dictionary Attack uses a list of common passwords, guessing one at a time, until the password matches or the list is exhausted. A Brute Force attack attempts all possible passwords of a given character set. A Dictionary Attack is the better choice for Online Password Cracking, due to the slow speed of attacking an online network service.
There are common password lists available online. One popular list, “rockyou.txt” contains over 14 million passwords. Rockyou.txt contains real passwords compromised in the “RockYou!” social application hack. Many of these passwords would pass modern password complexity checks. https://techcrunch.com/2009/12/14/rockyou-hack-security-myspace-facebook-passwords/
Why Do Online Password Cracking?
Network applications, such as custom web applications, are often the weak-underbelly of the network. Many times, the operating system and its services themselves will be hardened against attack, but the web service itself may have weaknesses, such as a SQL Injection or Operating System Command Injection, that can be exploited to gain further access. An attacker will attempt to accomplish two goals to get access to a system: upload a file and execute that file. Many web and network applications provide that functionality to legitimate users. So, if an attacker can gain the credentials of a legitimate user, he or she can then leverage any capabilities offered to legitimate users to gain further access. Finally, many servers only expose a single service to its legitimate users; gaining access to that service may be the only way in to a network.
What Are the Advantages of Online Password Cracking?
The primary advantage of Online Password Cracking is that an attacker does not need special privileges to initiate the attack. The computer being attacked is providing some service to its legitimate users, and a successful Online Password Cracking attack will allow the attacker to have the same privileges as the user whose credentials were guessed.
Secondly, there is a wide variety of protocols that can be attacked. Any network protocol that accepts a login and password can be attacked with Online Password Cracking
Finally, Online Password Cracking can be initiated literally from anywhere in the world over the internet, from any computer that has network access to the service being attacked.
What Are the Disadvantages of Online Password Cracking?
The primary disadvantage of Online Password Cracking is that it is very slow. Network speed, the speed of the service response, or built-in delays can limit the effective speed to hundreds of guesses per second, all the way down to single digits per second, or maybe even multiple seconds per guess.
Online Password Cracking attempts are very noisy. Most network services have log files that keep track of login attempts. An Intrusion Detection / Prevention System (IDS/IPS), a Web Application Firewall (WAF), or even an alert system administrator, can often spot these attacks even while they are in progress.
Finally, Online Password Cracking attacks can trivially be stopped by increasing the amount of time between unsuccessful login attempts (say, to five seconds or so), or better yet, by locking out the account after a few unsuccessful attempts. The account could be automatically re-enabled after a period (say, fifteen minutes), or for very sensitive accounts, the account could require an administrator to manually unlock it.
What Tools are Available for Online Password Cracking?
There are a number of tools available for Online Password Cracking. Four of the most popular are:
-
hydra (https://www.thc.org/thc-hydra/ … note that some browsers will alert on this page as “potentially unwanted software”) – a popular, powerful tool with a large number of supported protocols and options, but with a somewhat complex and finicky syntax for HTTP(S) web forms; the other protocols are pretty straight-forward to attack.
-
ncrack (http://tools.kali.org/password-attacks/ncrack) – from the makers of nmap; It supports fewer protocols than hydra, but it has a command-line syntax similar to nmap.
-
Medusa – created as an intended replacement for hydra; is intended to be a speedy, massively parallel, modular, login brute-forcer, boasting “thread-based parallel testing,” “flexible user input,” and “modular design” as features. It does not support as many protocols as hydra, however.
-
patator – a Python-based password cracker with lots of protocols and flexibility, but which is still a bit buggy.
Taking hydra and patator as examples, let’s look at example command-line formats for each. Below is a very simple hydra example that is attacking a very rudimentary HTML POST login page. A more complicated page would require a more complex command line to account for things like session cookies and Cross-Site Request Forgery tokens.
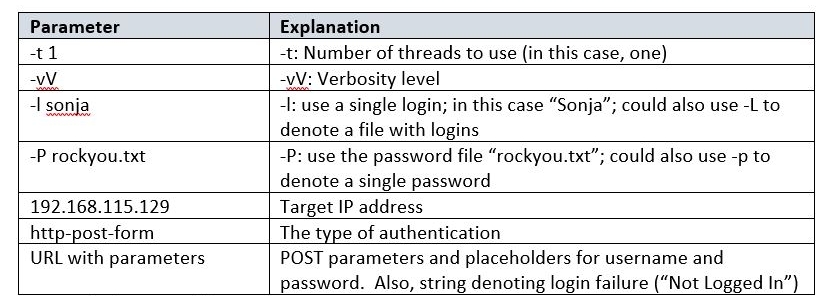
hydra -t 1 -vV
-l sonja
-P ~/rockyou/rockyou.txt
192.168.115.129
http-post-form
“/mutillidae/index.php?page=login.php:
username=^USER^&password=^PASS^&
login-php-submit-button=Login:Not Logged In“
The explanation of the parameters is shown in the table below:
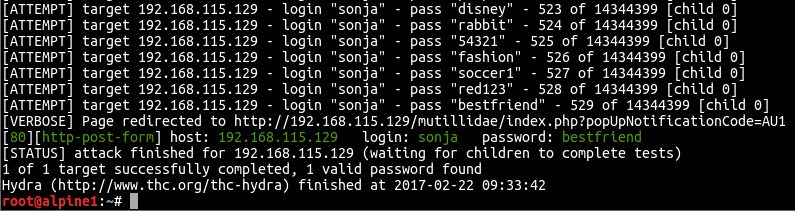
Here is a screenshot of hydra’s results from the above command line:
An example of how to use patator to attack an FTP server is shown below:
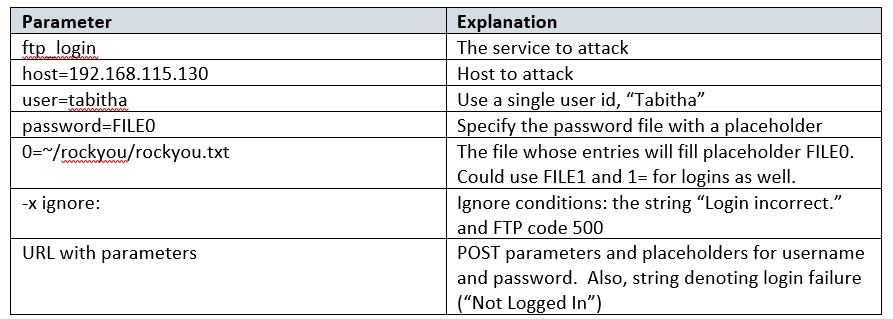
~/patator/patator.py
ftp_login
host=192.168.115.130
user=tabitha
password=FILE0
0=~/rockyou/rockyou.txt
-x ignore:mesg=’Login incorrect.’
-x ignore,reset,retry:code=500
The explanation of the parameters is shown in the table below:
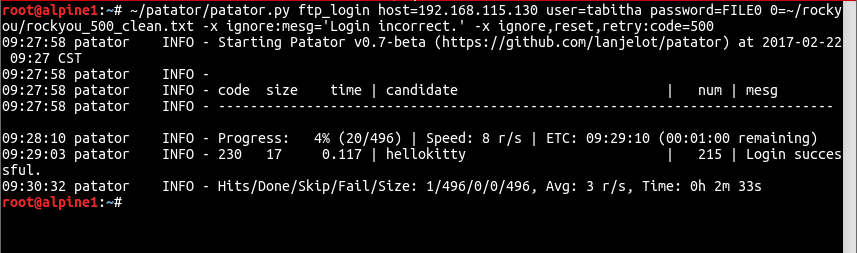
Here is the screenshot of the results from the patator command shown above:
Conclusion
Passwords are already a weak form of authentication. If a user is using a password so weak that it can be recovered by a slow, online attack, that’s a real problem! But even “strong” passwords, if they have been recovered from a breach such as the RockYou! hack, are still vulnerable to cracking. The best defense against an online attack is to lock out the attacked account after a handful of unsuccessful login attempts. Not only can this stop an Online Password Cracking attack dead in its tracks, it can also alert an administrator that such an attack is being carried out.
Author Bio
Daniel “Doc” Sewell works as a Lead Cybersecurity Engineer and Trainer for Alpine Security. He currently holds nine security-related certifications, including EC Council Certified Security Analyst (ECSA), Offensive Security Certified Professional (OSCP), Certified Information Systems Security Professional (CISSP) and Certified Secure Software Lifecycle Professional (CSSLP). Doc has many years of experience in software development, working on web interfaces, database applications, thick-client GUIs, battlefield simulation software, automated aircraft scheduling systems, embedded systems, and multi-threaded CPU and GPU applications. Doc’s cybersecurity experience includes penetration testing a fighter jet embedded system, penetration testing medical lab devices, creating phishing emails and fake web sites for social engineering engagements, and teaching security courses to world-renowned organizations such as Lockheed Martin and the Hong Kong Police Department. Doc’s hobbies and interests include home networking, operating systems, computer gaming, reading, movie watching, and traveling.